Link of the box: Mirai
Enumeration (NMAP)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
nmap -p- -vvv -n --min-rate 5000 -T5 10.10.10.48 -oN ports
Starting Nmap 7.91 ( https://nmap.org ) at 2021-11-17 17:20 EST
Initiating Ping Scan at 17:20
Scanning 10.10.10.48 [2 ports]
Completed Ping Scan at 17:20, 0.17s elapsed (1 total hosts)
Initiating Connect Scan at 17:20
Scanning 10.10.10.48 [65535 ports]
Discovered open port 80/tcp on 10.10.10.48
Discovered open port 22/tcp on 10.10.10.48
Discovered open port 53/tcp on 10.10.10.48
Discovered open port 1595/tcp on 10.10.10.48
Warning: 10.10.10.48 giving up on port because retransmission cap hit (2).
Discovered open port 32400/tcp on 10.10.10.48
Discovered open port 32469/tcp on 10.10.10.48
Completed Connect Scan at 17:20, 22.18s elapsed (65535 total ports)
Nmap scan report for 10.10.10.48
Host is up, received conn-refused (0.16s latency).
Scanned at 2021-11-17 17:20:22 EST for 22s
Not shown: 57081 closed ports, 8448 filtered ports
Reason: 57081 conn-refused and 8448 no-responses
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack
53/tcp open domain syn-ack
80/tcp open http syn-ack
1595/tcp open radio syn-ack
32400/tcp open plex syn-ack
32469/tcp open unknown syn-ack
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 22.40 seconds
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
nmap -p22,53,80,1595,32400,32469 -sC -sV 10.10.10.48 -oN scan
Starting Nmap 7.91 ( https://nmap.org ) at 2021-11-17 17:21 EST
Nmap scan report for 10.10.10.48
Host is up (0.18s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u3 (protocol 2.0)
| ssh-hostkey:
| 1024 aa:ef:5c:e0:8e:86:97:82:47:ff:4a:e5:40:18:90:c5 (DSA)
| 2048 e8:c1:9d:c5:43:ab:fe:61:23:3b:d7:e4:af:9b:74:18 (RSA)
| 256 b6:a0:78:38:d0:c8:10:94:8b:44:b2:ea:a0:17:42:2b (ECDSA)
|_ 256 4d:68:40:f7:20:c4:e5:52:80:7a:44:38:b8:a2:a7:52 (ED25519)
53/tcp open domain dnsmasq 2.76
| dns-nsid:
|_ bind.version: dnsmasq-2.76
80/tcp open http lighttpd 1.4.35
|_http-server-header: lighttpd/1.4.35
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
1595/tcp open upnp Platinum UPnP 1.0.5.13 (UPnP/1.0 DLNADOC/1.50)
32400/tcp open http Plex Media Server httpd
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Server returned status 401 but no WWW-Authenticate header.
|_http-cors: HEAD GET POST PUT DELETE OPTIONS
|_http-favicon: Plex
|_http-title: Unauthorized
32469/tcp open upnp Platinum UPnP 1.0.5.13 (UPnP/1.0 DLNADOC/1.50)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 21.97 seconds
Exploitation
Since the machine is running pi-hole, we can assume that this is a raspbian OS, we can check if the default creds are being used. pi/raspberry
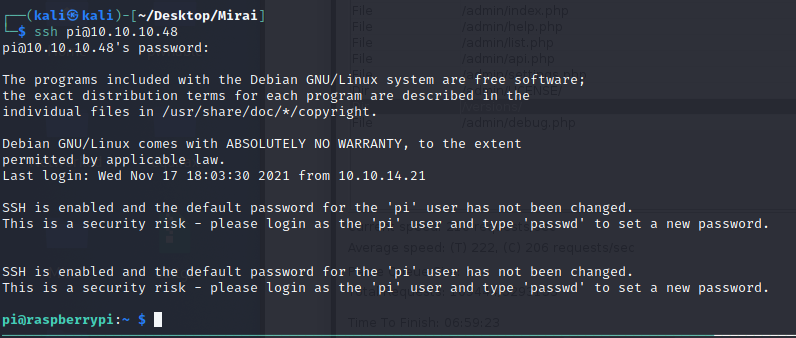
Inside the machine we can literally run any command as root.
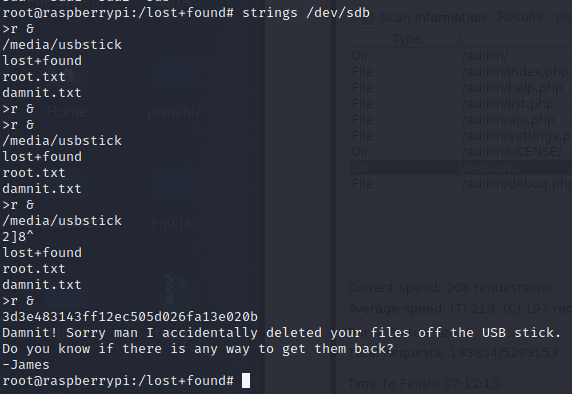
Inside the root folder there’s a message that the root.txt file in on the usbstick, but someone deleted it.
running strings /dev/sdb will get out our flag